OSEP - Advanced Evasion Techniques and Breaching Defenses - Review (2023)
Learn about my experience with the Advanced Evasion Techniques and Breaching Defenses Course & the OSEP exam!
Introduction
For the last three months, I've been working through the PEN300 course by OffSec which is all about advanced evasion and breaching defenses. Just got news from OffSec that I passed the 48-hour exam, and I wanted to share how I got the OSEP certification and what helped me along the way.
Overview of the Course (PEN300)
Programing Theory & MS Office
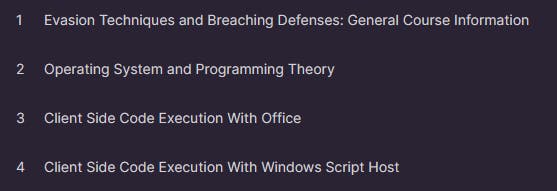
The PEN-300 course, focusing on Advanced Evasion Techniques and Breaching Defenses, spans multiple learning modules. The initial few chapters provide a general course overview, covering Operating System, Programming Theory and Client-Side Code Execution with MS Office.
Programming Theory forms a significant part of the course, exploring areas such as executing shellcode in Word Memory, PowerShell utilization, and the intricacies of client-side code execution. The course covers creating a basic dropper in Jscript, execution with Windows Script Host, and revisiting in-memory PowerShell techniques.
Antivirus Evasion
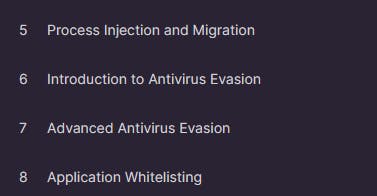
Process Injection and Migration introduce concepts like antivirus evasion, DLL injection, reflective DLL injection, and process hollowing. Practical considerations, such as simulating target environments, locating signatures in files, and bypassing antivirus with various methods, are also heavily covered to expand the student's understanding of antivirus evasion.
Antimalware Scan Interface (AMSI) bypass techniques using PowerShell and JScript were also covered. The module provides comprehensive strategies for bypassing AMSI. The Application Whitelisting section delves into theories and setups, exploring basic bypasses and techniques to overcome AppLocker restrictions using PowerShell, C#, and JScript.
Network Filters
Bypassing Network Filters covers strategies for overcoming DNS filters, web proxies, IDS and IPS sensors, and full packet capture devices. Techniques like HTTPS inspection, domain fronting, and DNS tunneling are explored in detail. Domain Fronting was one of my favorite sections of the course.

Post Exploitation
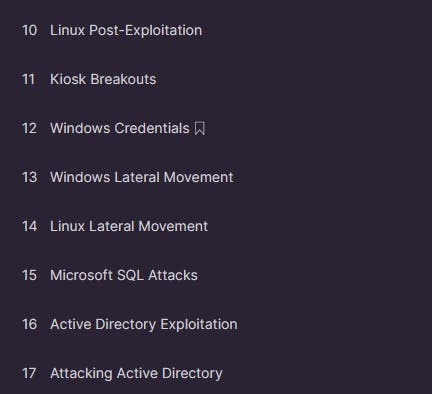
The course extends its reach to Linux post-exploitation, kiosk breakouts, and lateral movement. Practical insights are provided on Linux lateral movement, Microsoft SQL attacks, Active Directory exploitation, and SSH lateral movement.
Windows Credentials modules cover aspects like local and domain credentials, Kerberos, and post-exploitation processing. Techniques for lateral movement with Remote Desktop Protocol (RDP), fileless lateral movement, and exploitation of Microsoft SQL in Active Directory are also comprehensively explored in the later chapters.
My Preparation Journey
Course Module Labs
Alongside the PEN-300 course are the interactive labs that complement each section, providing hands-on experiences for students. These labs are aligned with the specific tactics covered in each chapter, allowing students to actively apply the newly acquired knowledge in a practical setting. I heavily utilized these labs to repeatedly practice the tactics taught in the section.
Challenge Labs
The challenge labs represent an extra layer of complexity beyond the interactive labs. Within these labs, students encounter six separate networks featuring a mix of Windows and Linux hosts operating in an active directory environment, all fortified with active antivirus (AV) protection (windows defender). Students are tasked with navigating through these challenging scenarios, putting into practice the skills and techniques acquired throughout the course.
The challenge labs serve as a practical assessment, requiring students to apply their knowledge to overcome real-world obstacles, providing a comprehensive test of their proficiency in techniques taught throughout the course. I personally made full use of these 6 networks to try out various TTPs taught and used it as my own cyber range.
External Labs
I personally didn't utilize any external labs other than a tiny AD lab I have in my home lab. However, many past students I spoke to, recommended the Hack the Box Pro Lab, Cybernetics for some extra practice. Alot of the students I spoke to, told me that this was a very good addition to challenge labs and helped them gain more confidence with their methodologies.
Course Content
I was going through the content at a steady rate alongside the specific chapter's labs. I preferred doing it as I was learning compared to some students who read through the content completely before heading to the labs for some hands-on.
Challenges and Learnings
C
I wasn't particularly proficient in C#, especially when it came to building loaders and bypasses, which were emphasized in the course. However, I found that I didn't need an extensive knowledge of C#. Basic skills in the language, coupled with a solid understanding of fundamental antivirus (AV) bypass techniques, were sufficient for me to navigate through the challenges presented in the course.
Macros
Handling MS Office Macro malwares proved to be quite challenging in my personal experience, especially with MS 2016 as it spawns into a 32-bit context. The migration to another 64-bit process without a C2 framework added an extra layer of annoyance. Nevertheless, the course provides a foundational understanding, covering the basics. This knowledge is adequate for students to build upon and extend into a practical working solution.
Applocker + Constrained Language Mode
Navigating around Applocker and Constrained Language Mode presented a variety of options, which initially proved confusing for me, given that it was my first encounter with both simultaneously. However, after experimenting in the labs and learning through trial and error, I managed to find efficient solutions. It turned out to be a rather enjoyable challenge once I got the hang of it.
The Exam
Exam Network
The exam consists of one large network with multiple machines that must be compromised. Students are given 48 hours (47 hours and 45 minutes to be exact) to complete the examination and another 24 hours for report writing. The exam objective provides detailed explanations on how a student can pass the examination. In general, you must have 10 flags each worth 10 points.
The student would have to first obtain a foothold and then perform additional internal attacks following the initial compromise. There are multiple attack paths through the network that will result in the same level of compromise.
Some of the machines will require multiple exploitation steps, resulting first in low-level local access, and then in root or administrative privilege escalation. Other machines will be fully exploitable remotely.
-offsec
In my personal experience, I found the difficulty level of the exam to be reasonable when compared to the content covered in the course. Everything necessary to pass the exam is included in the course materials; you just need to make a few extensions to your understanding and skills.
Tips for Future Test-takers
Tools
Throughout the course, various tools and techniques are introduced. If you lack a tool or if it's an open-source tool without a public release, ensure to pre-compile and test it in the labs before the exam. Avoid wasting valuable time during the exam on these tasks.
Techniques
There are multiple ways to get to the same destination. Try every possible method/tool/technique to achieve the same goal. Things that work in certain environments do not work in others. I learnt this the hard way. Thankfully it was in the labs instead of the exam.
For instance, one of my interactive CLM bypasses refused to work in one of the labs and my interactive shell would simply die. However, running the commands in a PowerShell Runspace would succeed. Things like this I would've never known if I hadn't tried.
Labs
This is an obvious one. Redo the labs and practice note taking alongside. Doing it once doesn't suffice (unless you're doing this as your day job).
Conclusion
In conclusion, the journey to obtaining the OSEP certification through the PEN-300 course has been a challenging yet immensely rewarding experience. Over the course of three months, I delved into advanced evasion techniques, breached defenses, and honed my skills in a dynamic and practical setting.
The exam, while appropriately challenging, proved manageable with the knowledge gained from the course. The emphasis on practical skills and the provision of necessary resources within the course materials made the exam preparation a smoother process. A piece of advice for future test-takers: familiarize yourself with tools beforehand, avoiding unnecessary hurdles during the exam.
Overall, the OSEP certification journey has not only expanded my technical capabilities but has also instilled a problem-solving mindset crucial in the realm of offensive security.