
It's been a goal of mine to conquer the certification and to be able to write this blog post by the end of 2021! I guess my time has finally come. I'll be talking about my OSCP journey and the path I took to attain the certification! I'll also be sharing some useful resources that I held close to myself throughout my journey. Lets get right into it 😊
An OSCP has demonstrated the ability to use persistence, creativity, and perceptiveness to identify vulnerabilities and execute organized attacks under tight time constraints. OSCP holders have also shown they can think outside the box while managing both time and resources.
Timeline
109 Days Spent Trying harder
07th March 2021 --> Start of PWK Labs
07th June 2021 --> End of PWK Labs
22nd June 2021 --> 1st OSCP Attempt
23rd June 2021 --> Good news from offensive-security
Background
About me
I'm a 20-year-old Cybersecurity student who has a strong passion for penetration testing and Vulnerability Assessment! I stepped into this industry roughly 3 years ago when I started embarking on my diploma in Cybersecurity & Digital Forensics.
Prior Knowledge
Prior to my OSCP Journey, I had attained a couple of certifications that helped me throughout my journey. I had:
Red Hat Certified System Administrator (RHCSA)
Certified Ethical Hacker (ANSI)
Certified Ethical Hacker (Practical)
Fortinet Network Security Expert 1 & 2 (NSE)
These were some of my certifications which were very helpful throughout my journey! I started maining Linux about 2.5 years ago. (Using Linux daily. Not as my main OS I can't give up my adobe suite and office365) Which was also when achieved my Red Hat Certified System Administrator. This certification really made me understand the INs and OUTs of Linux. I had finally gotten the hang of a terminal and was able to use it as if I was navigating through GUI.
About a year and a half ago, I started getting into HackTheBox, TryHackMe and VulnHub. This was also when I was taking an ethical hacking module @ school. These got me really interested in vulnerability analysis and the art of penetration testing! During that period, there were more and more people in the cybersecurity community attaining the cert and posting about their experience which got me even more hooked. That, together with the awesome cybersecurity content creators pushed me over the fence and into the field!
I knew I was setting myself up for failure if I jumped straight into OSCP during that period. Thus, I took up CEH ANSI and CEH Practical (ikik 😢 I'm sry) while training passively for the end goal! (OSCP). After I completed those two certifications and got out of my internship, I took a short break and got to work on OSCP 😈!
Penetration Testing with Kali Linux
I initially started off the course timeline by spending my days going through the PDF. I was doing every single chapter including the initial ones. After some time passed, I realized that I was just wasting my time by doing that 😭. Other people's perspectives on this might be different. However, I felt like I was just doing things that I already knew or had knowledge of.
Thus, I decided to skip through the chapters and their exercises and ended up focussing only on those chapters where I was really lost and had no clue about what I was doing. AKA Windows 🤡 After I had picked off the chapters I decided to ignore, I ran through the PDF pretty quickly.
OSCP Labs
Lab Time --> 90 Days
Lab Owns --> 75/75 machines
AD networks owned --> 2/2 Networks
Hidden networks unlocked --> 3/3 Networks
10/10. Hands down. I have never done a lab as sophisticated and value-adding as this one. There were just so many opportunities to learn, served to me on a platter. It was filled with a ton of content. No two boxes had the same path.
But then again, that doesn't mean that it prepares you for the examination. The labs had Active directories/tunneling techniques/boxes that are there just to kill you. They definitely teach you a lot. However, some have said that it teaches more than what you actually need for the exam. In my opinion, I felt that it was fine because I enjoyed the process of going through and breaking the boxes and gaining valuable knowledge at the same time.
External Labs
PG Practice --> 51 Machines
Hack The Box --> 40 Machines
VulnHub --> 8 Machines
External Labs were a hugeeee part of my preparation. There are a ton of platforms offering hundred of machines. From my analysis, I noticed that different people had different opinions on these platforms. I ended up at least involving 2 of these platforms in my practice.
Proving Grounds Practice – had about 63 machines in total at the time of my enrollment. I really liked their platform and machines. The platform was simple and machines' difficulty was fairly graded. They had 3 main categories. Easy[10 points], Medium[20 points] and Hard[25 points]. During my month's subscription, I managed to clear all their Easy and Medium Boxes on top of 4 Hard boxes. I'd say I PG trained me to look through any noise/unrelated services. They tend to have more than just the vulnerable services. This really prepped me well for the exam
Hack The Box – I did 40 machines in HTB during my training period. These boxes thought me more of the methodology in terms getting through a machine. It also had some unique exploits and pathways. At the end of the day when you've gone through quite a number of boxes. It is all the same process and you just have to be able to identify the vulnerability.
External Resources
I can't say this enough. The cybersecurity community is a godsend. There are so many awesome people in the community and are willing to share knowledge with you! There are also a ton of awesome cybersecurity content creators who provide the community with an insane amount of free resource and guidance
Content Creators
Technical Resources
Discord Servers
Buffer Overflow
The Buffer Overflow box in the exam is literally a giveaway! I spent hours making sure I'm able to complete this within 45 minutes. This is to ensure that I have the maximum amount of time for the rest of the boxes and also to secure 25 points with ease. The methodology for stack-based BOF is almost always (99.999% of the time) the same! So I'd advise you to master this if you're sitting for the exam! I'll probably post a step-by-step walkthrough of my BOF methodology sometime next week. (done, here u go!) Keep in mind, there are a ton of resources for this, and here one that I think is the best!!
[
TryHackMe | Buffer Overflow Prep
Practice stack based buffer overflows!

TryHackMe
![]()
](tryhackme.com/room/bufferoverflowprep)
Time Management
This was something I didn't have (for anything except OSCP). I literally cut out everything I used to do. I stopped gaming, hanging out with friends, talking to people on the daily, lost sleep, and more. However, this turned out to be a plus point for me at the end of it all. There were definitely times where I saw people doing things that seemed fun and would wish that I could be with them but I told myself I could do that anytime but not this. I totally do not recommend this way of working. It was highly taxing on me and I wish I'd taken a bit longer and been more relaxed. I definitely overworked myself like crazy by doing **174 vulnerable machines** in 100-ish days. I recommend you guys to take it a little slower if you're planning to take this certification!
Note Taking
I can't stress this enough! Note. Taking. Is. The. Most. Important. Part. Of. The. Process. You never want to look up the same thing twice. I HIGHLY recommend a proper note-taking software and template! Doing a box? Take notes. Found a new privilege escalation method? Take notes. Literally, take notes of everything you think u might need. Never leave room for gaps at all. I struggled with this during the initial days of the course. I always brushed it off. I'd randomly spam my discord with links which I'd forget about in a day or two, take a screenshot of a box while I'm doing it and never review it or just not take notes at all. (All this was when I had a primary note-taking software). A couple of weeks in, I realized my mistake and started correcting them. However, it was really hard to remember past machine's methodology and rewrite them down. So please do it!
My note-taking tool of choice is Notion.so. They are hands down the best note-taking software I've used. They literally have everything u ever need. From code snippets to coloring to cross-platform sync and way more. There are too many things to fit in this post 😂. TRY IT OUT for yourself and you'll thank me! (I hope)
[
Notion – The all-in-one workspace for your notes, tasks, wikis, and databases.
A new tool that blends your everyday work apps into one. It’s the all-in-one workspace for you and your team.

Notion

](notion.so)
Workstation
I'm someone who values setups and screen real estate like crazyyy. I'm sure there's someone out there that hates me for how much I talk about hardware/setup building/keyboard customizing/buying gear. To whom it may concern: I'm Sorry.
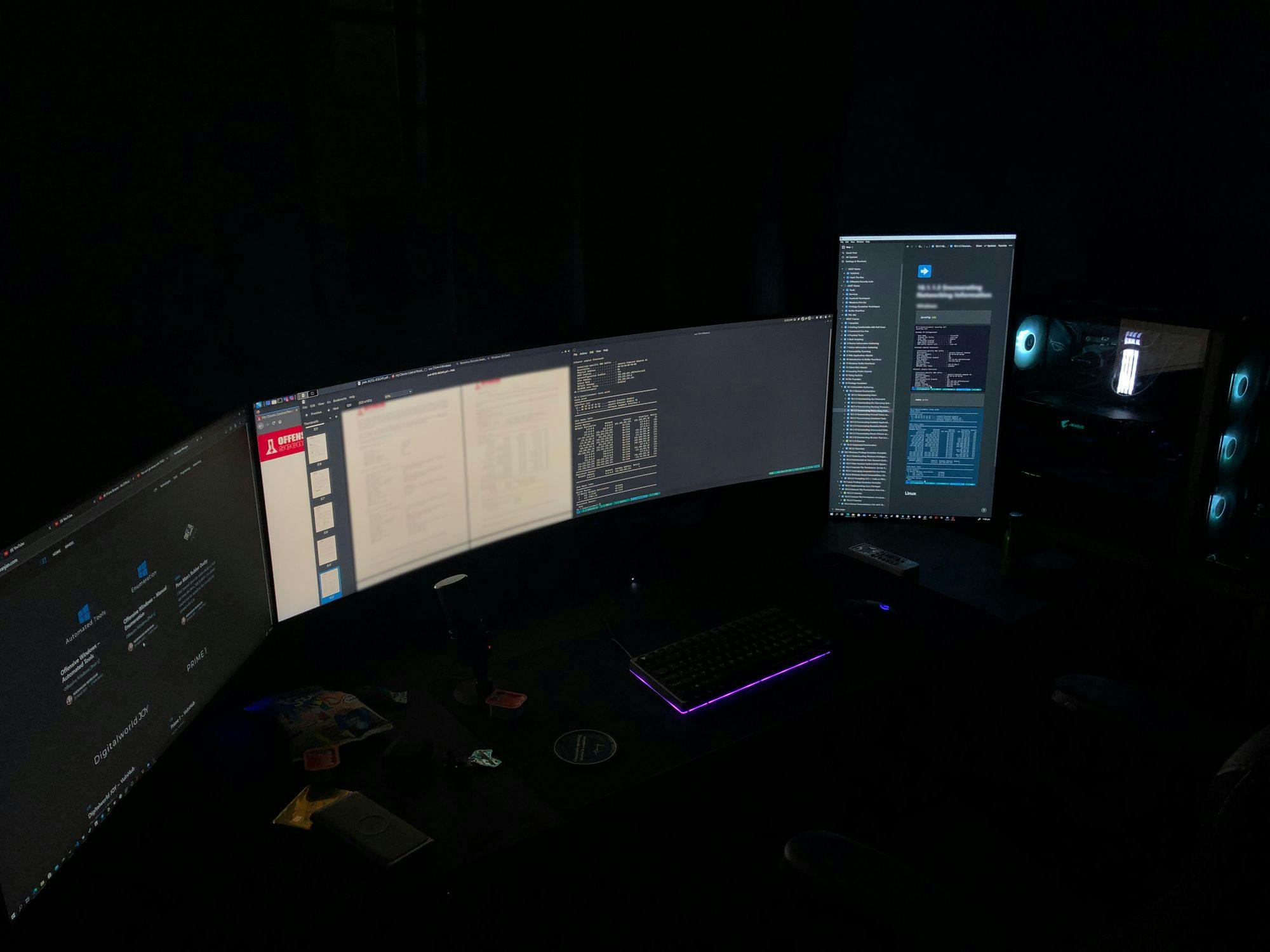
I've cleaned it. Source: Trust me bro
This here was my workstation throughout my OSCP journey. I value my workstation area more than I should. I personally feel that I'm in my prime when I have a conducive and quiet environment with all the gear and screen real estate I need. I can't remember doing a single assignment on my laptop throughout the last 3 years. Others' opinions might defer but this is me 🙏. And yes, I definitely only use my gpu for cracking
CPU – i7 9700K RAM – 32GB GPU – RTX 2080 STORAGE – NAS for tons of files & SSD for VMs and Windows Center 49inch – Main OS I'm using Left 27inch Horizontal – Research purposes Right 27inch Vertical – solely note taking
👿D-Day👿
I'll be honest, I'm not a morning person AT ALL 😂. Those who know me, know that I sleep through the day and work through the night alone. I'm never reachable during a proper day (I'm sorry).
I booked my exam at 1 PM for the 22nd of June. I didn't do anything related to security the day before the exam! I was extremely nervous the night before and couldn't sleep in peace. I was super restless through the whole night.
On the exam day, I got up at about 11 am, ate breakfast, chilled for a little, and locked myself into my setup. Booted kali, notion, and the proctoring software. I was going ̶s̶i̶c̶k̶o̶ panic mode.
Proctoring setup
Unlike other experiences I heard, my proctoring setup process went pretty smoothly. Within 12 minutes I was done with ID verification, room check, camera placement. A small word of advice....Make sure the camera you're using has autofocus or is HD. My camera was 720p30fps. Sadly, it didn't have autofocus and my camera just wouldn't show my ID with any kind of clarity.
This was on me, not offsec. I quickly pulled out my phone, enabled debugging mode, launched iriun webcam and managed to save myself. Recovery: 100. After that, I was done and I still had 4 minutes to spare. 4 minutes later, I received my VPN pack. I had to run a bash script to test the VPN's connectivity and I was off to the races.
Buffer Overflow
Like I mentioned earlier, this is a giveaway. I ran through this challenge in 46 min. That was slightly longer than what I intended but I was glad I didn't run into any issues!
10 Pointer
This box was pretty straight forward and PG Practice's Easy section helped a lot!! I was able to get root on this box in 32 min.
20 Pointer
User access on this box took me another 32 min and it took me 2 hours to get root. This box was fairly confusing with the services but I'd say it was manageable with all the resources I had gathered from the OSCP labs.
20 Pointer
User access on this box took me 1 hour 49 min and it took me 1 hour 25 min to get root. Doing those external labs & fiddling around with Linux myself randomly definitely came in handy for this one!
Breaks
I took a total of 2 breaks during the 7 hour time period. Both were around 15 minutes. The first break was when I couldn't land a user on the first 20 pointer and the second break was when I couldn't root the second 20 pointer.
Sleep
I requested the proctor to pause camera at about 2am~ish but I only ended up sleeping for about 3 hours.😂 I really couldn't sleep cuz I didn't believe myself and kept telling myself I missed something.
Next 17 hours
I gave the other 25 pointer a shot multiple times during the 17 hours I had left, but it never budged. I thought I almost had it thrice. But I ended up not getting it sadly 😢. I redid those 4 boxes I completed, about 4 times just because I was that paranoid. First rerun, I spent filling in the gaps that were existent in my notes. second rerun, I did the same thing. 3rd rerun, I spent redoing only with my notes as a reference and closed every other reference I had open on the box. Last rerun was just me being extremely paranoid.
Overall Timeline
12:45 – Setup Proctoring sesh
13:00 – start of exam
13:46 – 25 Pointer rooted [BOF]
14:18 – 10 Pointer rooted
14:50 – 20 Pointer user
16:45 – 20 pointer root
18:34 – 20 Pointer user
19:59 – 20 Pointer root

Offensive Security
Service
Solid. They were very clear since the day I registered for an account. From the purchase process to the final exam I had zero issues with the team. Everything was smooth sailing and I was really happy with their service! They were very informative with email and the offsec officials in the discord were friendly and helpful!
Support
This is another point for offsec. During my lab time, they released 5 retired exam boxes into the lab. When that happened I was at my last 7 days of lab. So I decided to attempt these 5 retired boxes and was stuck on one of them for the longest time and I was very sure that I had the right exploit path. So, I approached the staff in the discord, and 3 of them were super nice to re-exploit the machine on their end and confirm that there really was an issue on their end. They then pointed me to their mail support. I explained my situation to them and they indeed confirmed the issue and were very generous to extend my lab time for 2 days so that I would have enough time to complete the labs. (That was the time I lost debugging 😭) But, kudos to offsec for covering me on that one. 💯
Conclusion
I'm glad I got through this journey and learned soo sooo much! And I'm excited for you to go geddit! Don't sweat it. It might seem like a huge feat at the beginning. But as u progress things will smooth out and you'll see yourself getting the hang of it. I'd like to thank each and everyone who gave me any kind of support throughout my journey from the bottom of my heart!! You guys know who ya'll are!! This is just the beginning for us!!😊😊

