Introduction
Having spent a considerable amount of time immersed in web-related attacks in the AWAE labs over the last 4 months, I began to feel a sense of detachment from the realm of Active Directory (AD) exploitation and pivoting. Now that I was done with the web attacks for the time being, I wanted to return to the Active Directory side of things and was looking for something to help hone my skills in this domain (haha...). That's when HTB's CPTS popped back into my radar. I initially came across the CPTS roughly 9 months ago when it was first announced.
HTB Certified Penetration Testing Specialist (HTB CPTS) is a highly hands-on certification that assesses the candidates’ penetration testing skills. HTB Certified Penetration Testing Specialist certification holders will possess technical competency in the ethical hacking and penetration testing domains at an intermediate level. They will be able to spot security issues and identify avenues of exploitation that may not be immediately apparent from searching for CVEs or known exploit PoCs.
Having completed the course and cleared the exam, I felt compelled to share my experience and provide valuable insights for those who are interested in embarking on this journey or for those who are simply curious. As always I'll be splitting up the review into several parts.
Background
My experience with Active Directory (AD) has been a mix of exploration and hands-on learning. While my AD experience may not be extensive, I've built my own minimal AD environment in my home lab which allowed me to gain practical experience in setting up and configuring AD components, as well as understanding the intricacies of user management, group policies, and authentication mechanisms.
The greater chunk of my AD exploitation knowledge comes from the CRTO (Certified Red Team Operator) course which I had enrolled in last year which provided me with a deep understanding of the various AD attack vectors. From reconnaissance and privilege escalation to lateral movement and persistence techniques, I acquired a solid foundation in AD exploitation through the CRTO course materials. Even though the iteration of OSCP I took did cover AD, I wasn't evaluated for it on my exam.
On top of these, I passively engaged in various challenge labs that focused on AD from time to time. These helped with the labs and challenges throughout CPTS.
The Course

Penetration Tester Path
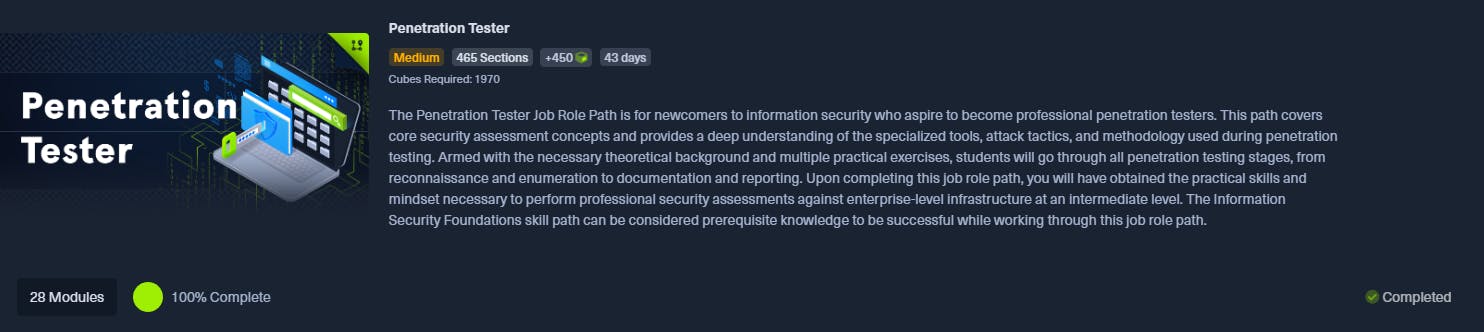
The Penetration Tester Job Role path is what you've to go through before being eligible to take the exam. This is the course that accompanies the exam. The course is extremely well put together and consists of the following domains:
Web attacks
Local Privilege Escalation (Windows & Linux)
Post-exploitation
Basic C2 (Metasploit Framework)
Active Directory Enumeration & Attacks
Pivoting & Lateral Movement
Penetration testing processes
Vulnerability Assessment & Reporting
👍The Good
The course content was of high quality and was accompanied by individual labs that apply the concepts taught in the module.
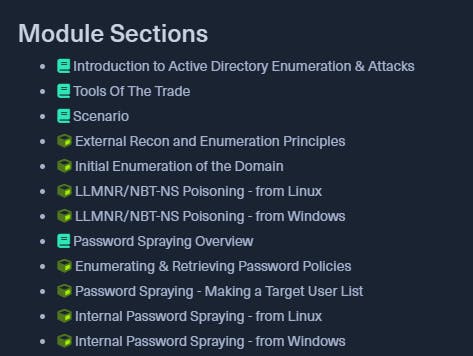
This is a snippet of some of the modules in the ACTIVE DIRECTORY ENUMERATION & ATTACKS section. Modules with the cube icon imply that they contain interactive labs to practice the theory taught.
There are roughly about 500 exercises and tasks that you'll go through while embarking on the penetration tester path. The course covers quite a number of domains and it does it well. Fundamentals are well explained and easy to understand. I learned a couple of interesting techniques from the modules given my experiences.
At the end of most modules, there's a Skills Assessment section which usually consists of a multi-part exercise or exercises of varying difficulty. The Skills Assessment does not come with a guided walkthru / theory writeups like other chapters. They consist of all possible attack vectors learned in the entire module. They are also a good gauge to see where you stand and if you're able to solve challenges without some form of hand-holding.
At the end of the course, you'll face this module called ATTACKING ENTERPRISE NETWORKS. This module covers all aspects of a penetration test from start to finish. You'll work through a simulated External Penetration Test resulting in internal network access and ultimate compromise of the Active Directory environment. Most importantly, this module walks through each and every step toward Domain Dominance. It's highly advised to go through this network without the walkthrough. It helps give an estimate of how ready you are for the examination.
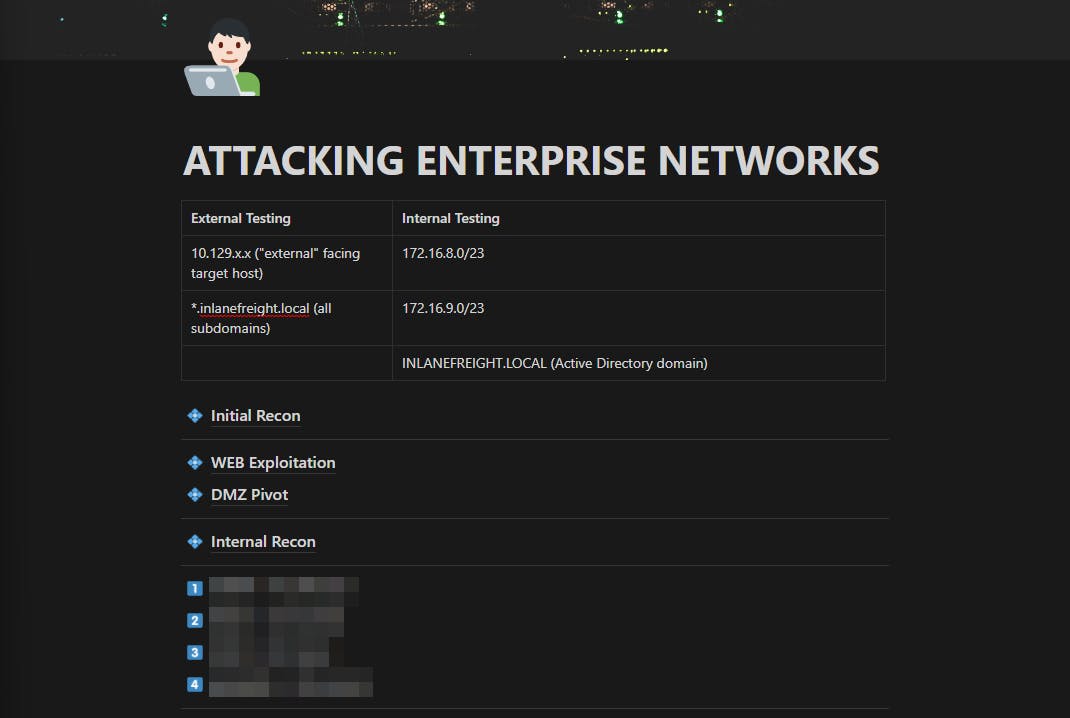
This network is also what I based the Ligolo-ng write-up on. Its a well-put-together lab that consists of web attacks, active directory exploitation, pivoting through multiple subnetworks and more. I personally enjoyed this end of course exercise. After going through it blind, I'd definitely recommend others to go through it a second time with the walkthrough. The walkthrough addresses some of the attacks that should be done while on an engagement even though they may not yield valuable results. This includes password spraying, LLMNR spoofing, kerberoasting all possible accounts and more. And as always, taking good notes throughout the practice engagement definitely helps in the exam! Though, being able to do this blindly might not necessarily mean that you're ready for the exam. Mileage varies based on experience!
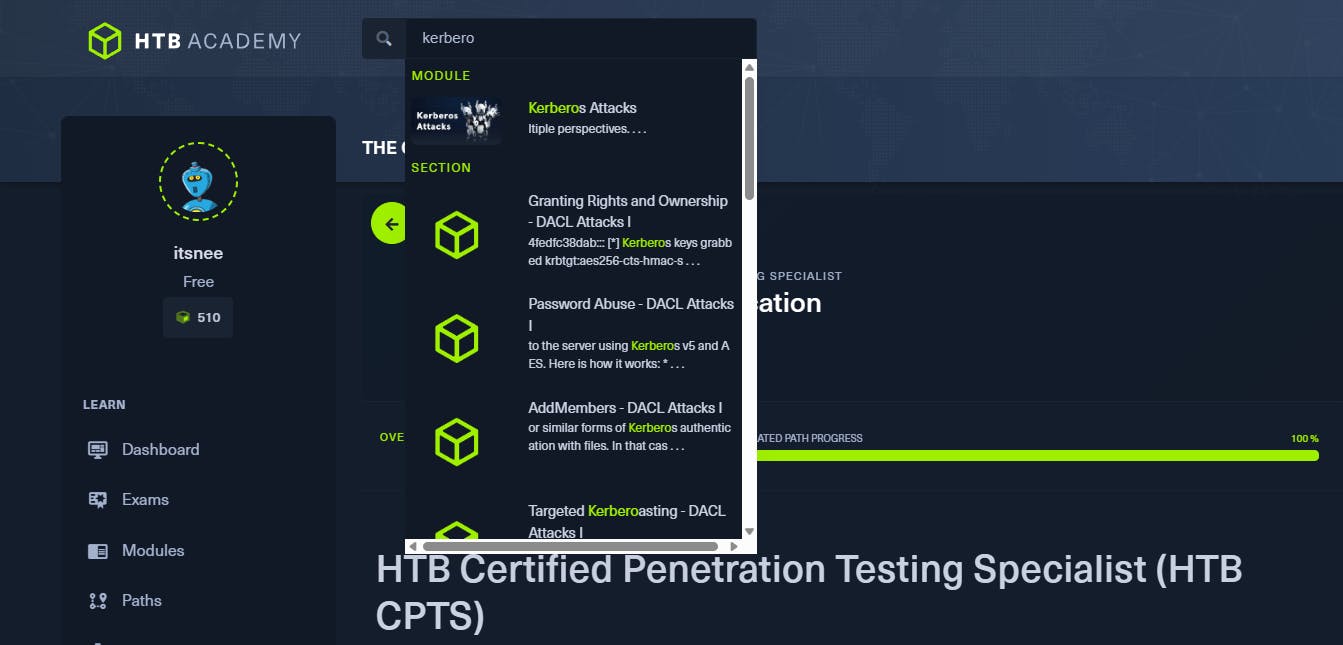
One of the best thing about the platform was the Global Search. This search allows students to search for anything site-wide. Super useful when it comes to finding a certain technique.
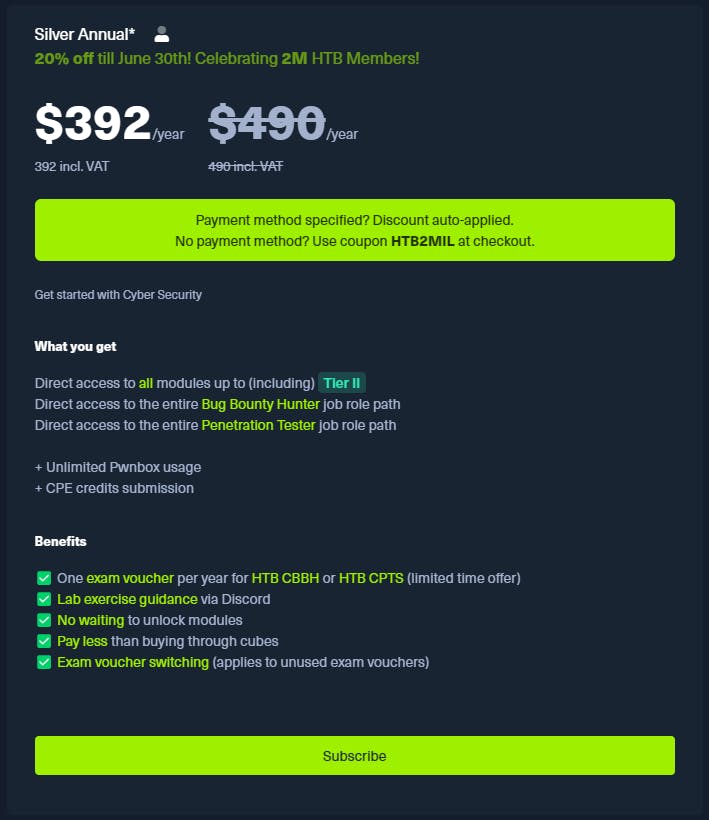
The HTB CPTS certification course not only offers immense value but is also priced exceptionally well. Each dollar spent on this course is truly worth it, considering the high quality and comprehensive content it provides. The attention to detail and the expertise of the instructors shine through every module.
You could pay the $490 to get access to all Tier II modules and an exam voucher (which comes with a free retake) or....
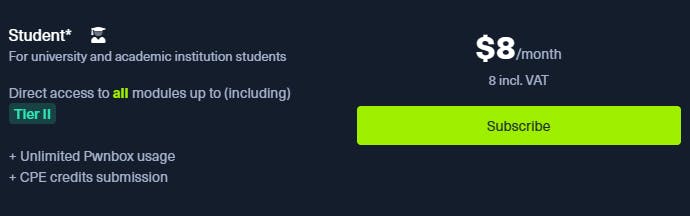
if you have access to your personal .edu mail, you could pay $8 a month for the same level off access and purchase the exam voucher separately for $210
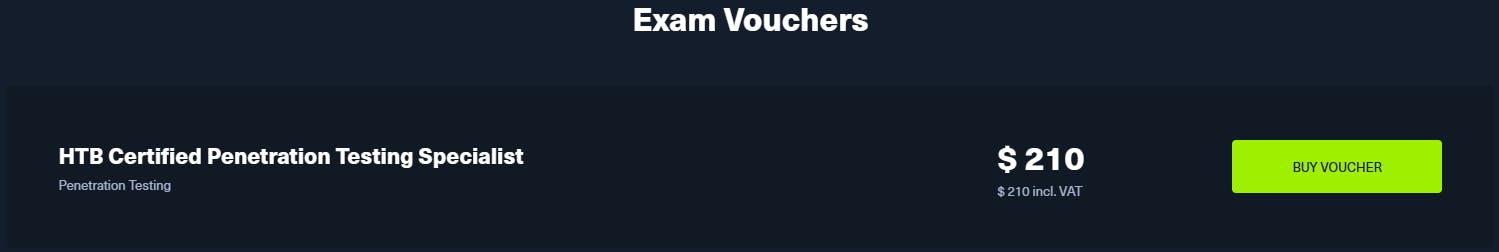
*All prices are in USD*
👎The Bad
My iteration of this section will probably be different from yours but hey here are things that I found to be iffy for me.
The Text
The course was a bit too wordy for me and I'm sure this is probably a me problem. I'm more of a visual learner and I prefer video walkthrough's where I can see things in action and learn.
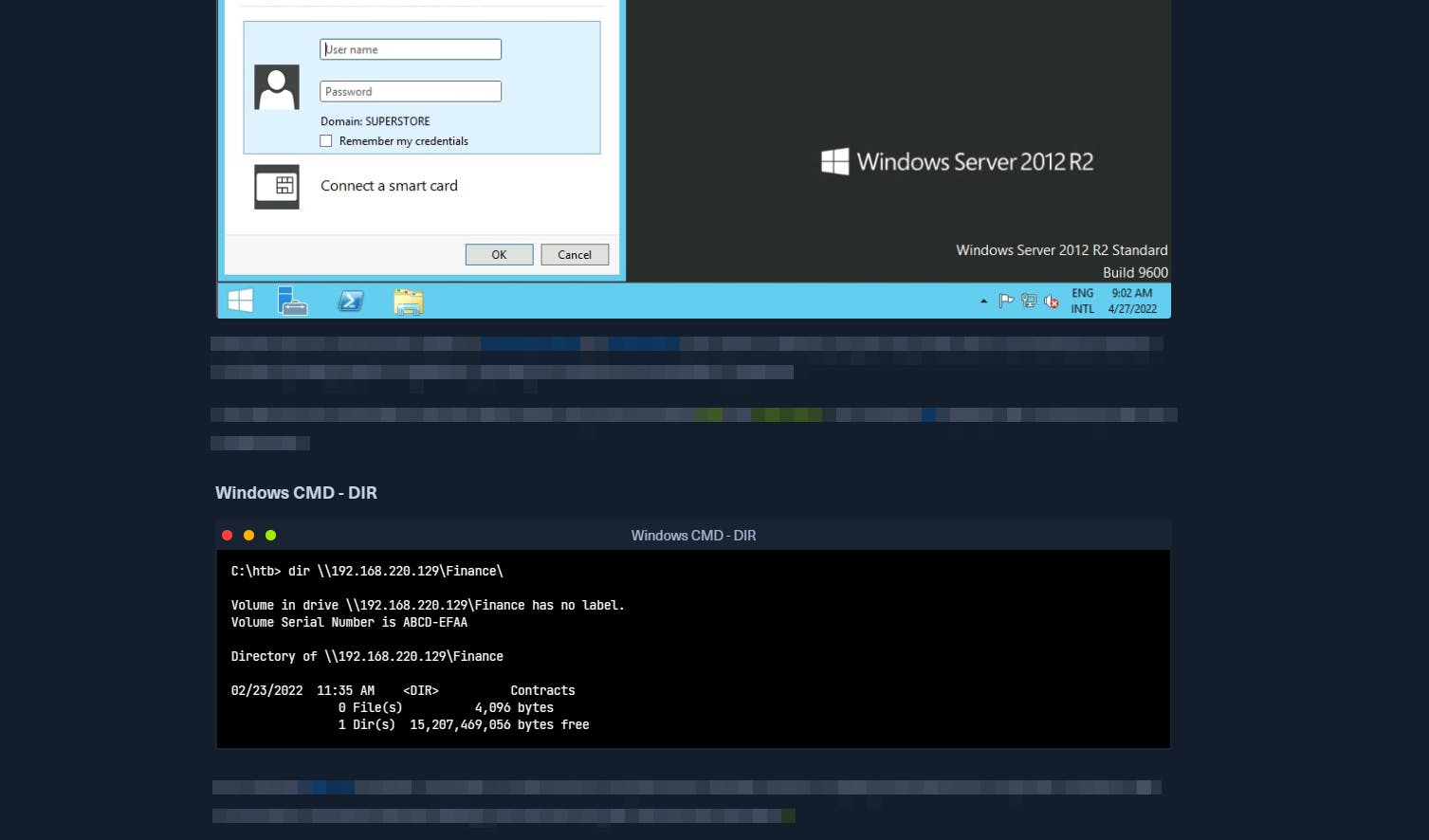
However, the course did have extensive screenshots and code snippets to make up for that. I'd still have preferred videos. Each to their own I guess.
Forced 100% Course Completion
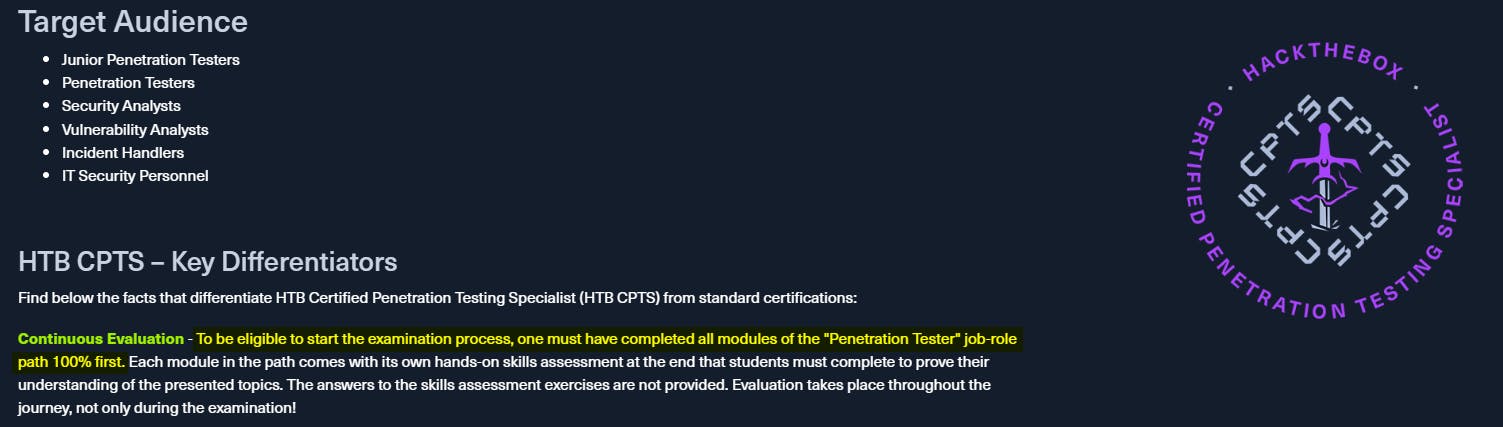
The other issue I had with the course was that students were forced to complete all tasks and challenge labs that come with the Penetration Tester job-role path before they could start the examination process.
This puts students with prior experience at a slight disadvantage. Experienced students would have to sit through sections that they are already well versed in and painstakingly complete the corresponding challenge labs.
I get why they're doing this but there should be some sort of opt-out program that helps seasoned students.
The Exam
About
The candidate will have to perform blackbox web, external and internal penetration testing activities against a real-world Active Directory network hosted in HTB’s infrastructure and accessible via VPN (using Pwnbox or their own local VM). Upon starting the examination process, a letter of engagement will be provided that will clearly state all engagement details, requirements, objectives, and scope. All a candidate needs to perform the required penetration testing activities is a stable internet connection and VPN software. HTB Certified Penetration Testing Specialist is the most up-to-date and applicable certification for Penetration Testers that focuses on both penetration testing and professionally communicating findings.
Candidates are given 10 days to complete the exam and the corresponding report. The exam consists of multiple networks (External & Internal). It covers most if not all domains taught in the course.
There are a total of 14 flags spread across multiple machines on the network which add up to 100 points. Candidates require at least 12 flags (85 points) with a comprehensive report to pass the examination. The general flow of the exam is very similar to the ATTACKING ENTERPRISE NETWORKS module but the complexity varies heavily.
My Experience
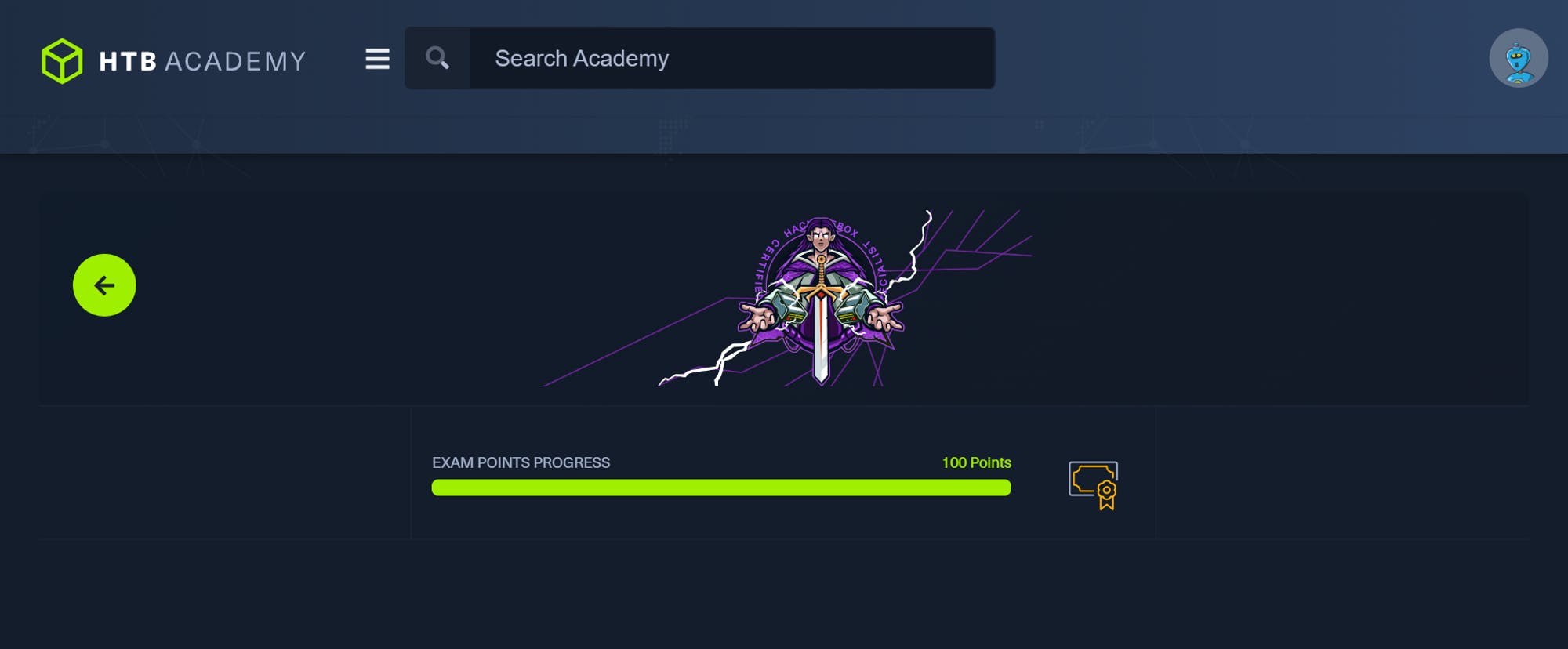
I cleared the exam with all 14 flags and 100 points. I personally used up all the time given for both the report and the actual exploitation.
The first couple of hours were pretty draining. Just extensive Enumeration of all services exposed and a lot of note-taking. I was also mentally coming up with diff paths that could be viable. Including some questionable ones (🤔).
After a couple more hours of enumeration, I had the ball rolling....or at least I thought so. There'd be one major move followed by a couple of minor steps which was simpler compared to the bigger hurdle.
Here's something a friend of mine said to me while I was stuck at one of the lateral move steps:
If you're stuck for too long on a single target, it means that you are stuck on a single way of thinking.
It's cliche but taking a break during those long hour sessions really does help. The exam lab is extremely well made and I found it to be pretty diverse in terms of attack vectors. Extremely comparable to other exams labs I've crunched through. Its right up there.
Overall, the exam is definitely challenging & draining but pushes the candidate to apply everything that was taught during the course. I don't think there was knowledge from any chapter that wasn't applied in the exam. The exam also teaches students time management and the importance of reporting.
Reporting
Reporting was a big thing throughout the exam. I've always been used to taking raw notes and reporting all at once at the end of the exam. I found that to be a bit exhausting this time around given that it was a comprehensive engagement. I plan to report as I go from now on. We'll see how that goes.
HTB Provides students with a report template and highly advises students to make use of their template as it sort of tells students what they're looking for and makes grading the exam easier for them.
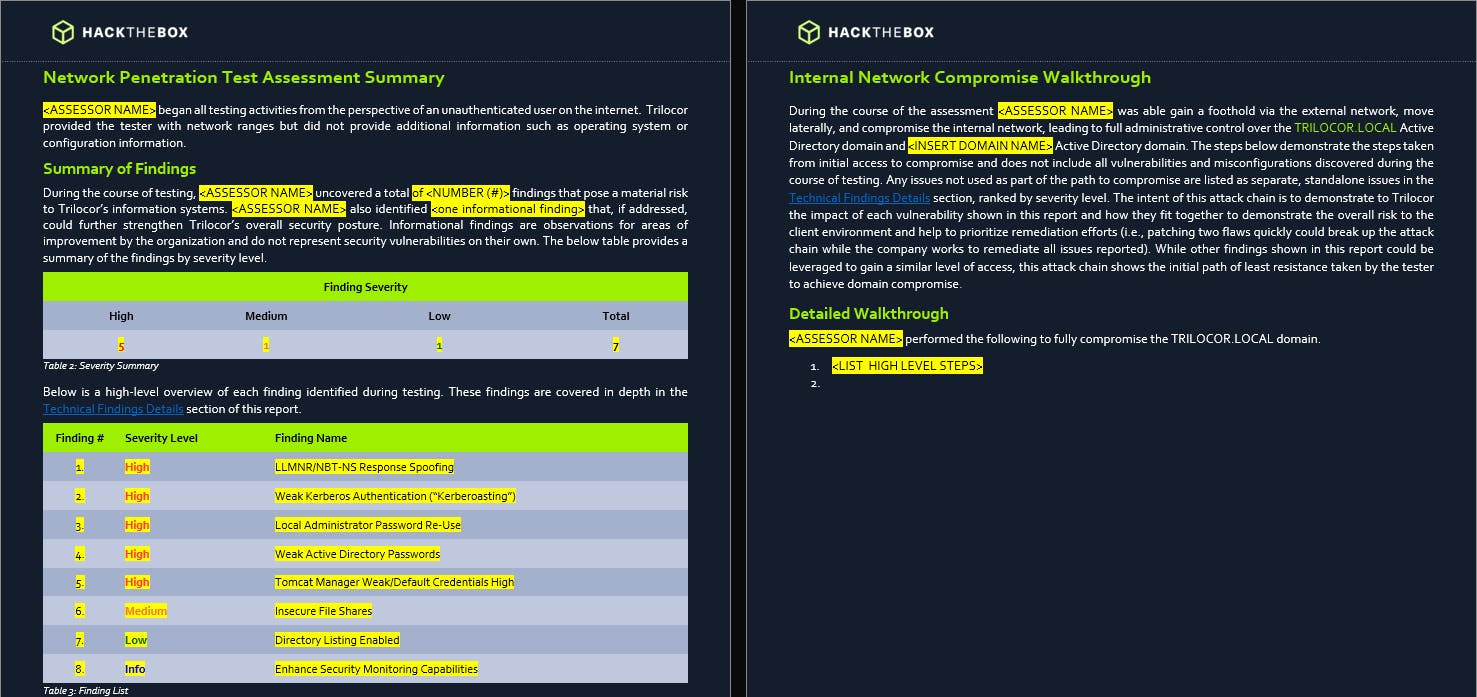
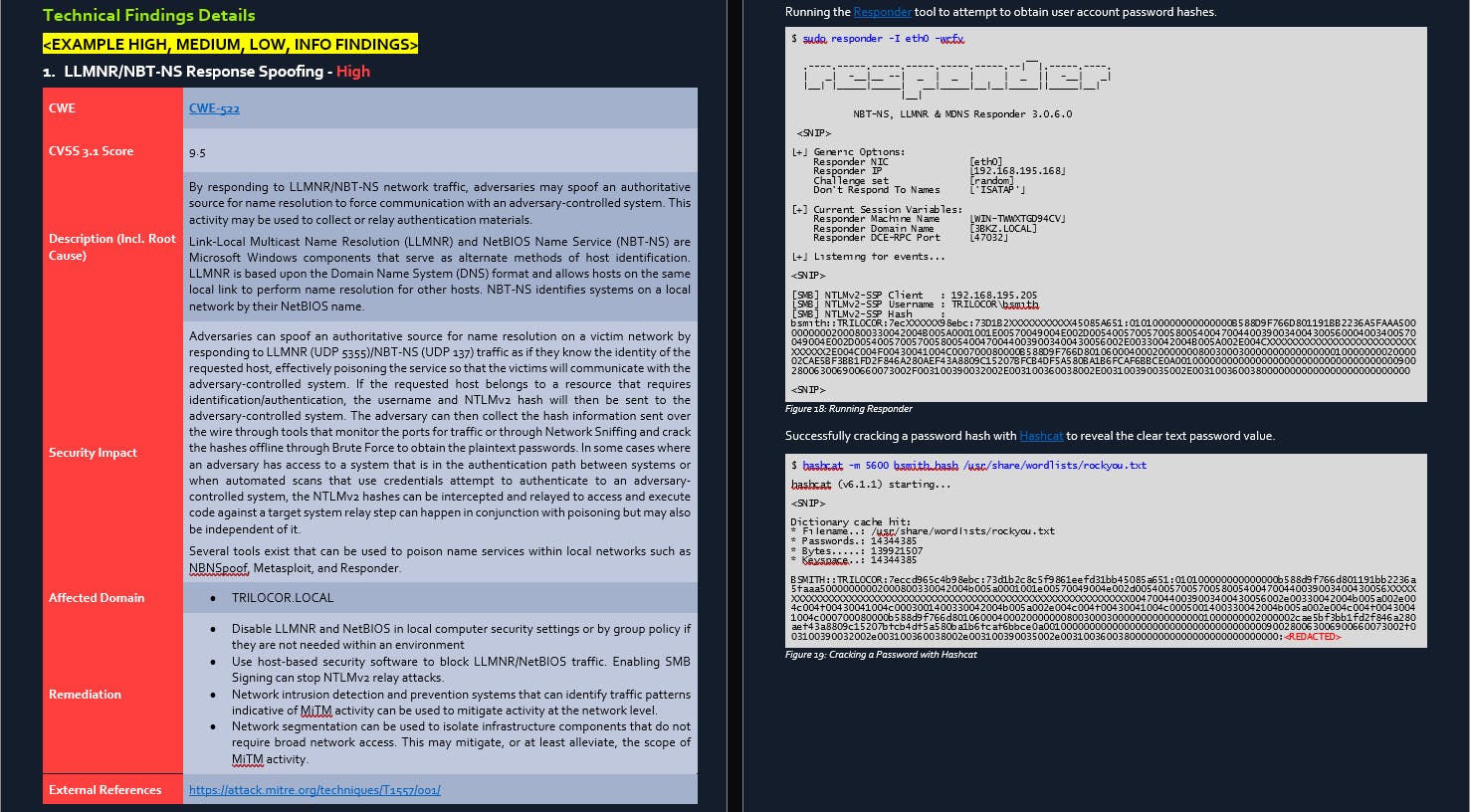
Here are a few snippets of the report template given to the students at the start of the examination. The report requires students to provide a full walkthrough of the engagement. Showcasing how the pentester went from having no access to gaining Root access / Domain Dominance.
Conclusion
In conclusion, the HTB CPTS certification has proven to be a valuable and transformative learning experience for me. This course has provided me with the opportunity to delve into the world of AD exploitation and address the areas where I felt a lack of knowledge. However, the course does cover more than just AD as mentioned in this writeup. The comprehensive curriculum and hands-on approach have allowed me to bridge some of the gaps in my understanding.
In summary, I recommend the HTB CPTS certification to individuals eager to deepen their understanding of offensive security (& AD Exploitation for that matter). This course provides a comprehensive and practical foundation for addressing various security challenges and honing penetration testing skills.
With that out of the way, on to the next! 😁

- Nee

