
This is my second CTF Writeup! I came across this CTF on one of the subreddits that I browse frequently. If you would like to give this CTF a try, u can do so by getting the resources from this link. This CTF contains 20 challenges from 4 different focus areas! | Crypto | Misc | Stego | Web |. Feel free to follow along! Lesgooo ☀
Crypto Challenges
Challenge 1 — Discord Bot
import logging import socket from typing import Optional import aiohttp from discord.ext import commands from prometheus_async.aio.web import start_http_server as start_prometheus_http_server from bot import api log = logging.getLogger(‘bot’) class Bot(commands.Bot): def init(self, args, **kwargs): self.connector = aiohttp.TCPConnector( resolver=aiohttp.AsyncResolver(), family=socket.AF_INET, ) super().init(args, connector=self.connector, kwargs) self.http_session: Optional[aiohttp.ClientSession] = None self.api_client = api.APIClient(loop=self.loop, connector=self.connector) log.addHandler(api.APILoggingHandler(self.api_client)) def add_cog(self, cog: commands.Cog) -> None: “””Adds a “cog” to the bot and logs the operation.””” super().add_cog(cog) log.info(f”Cog loaded: {cog.qualified_name}”) def clear(self) -> None: “””Clears the internal state of the bot and resets the API client.””” super().clear() self.api_client.recreate() async def close(self) -> None: “””Close the aiohttp session after closing the Discord connection.””” await super().close() await self.http_session.close() await self.api_client.close() async def start(self, *args, kwargs) -> None: “””Open an aiohttp session before logging in and connecting to Discord.””” self.http_session = aiohttp.ClientSession(connector=self.connector) await start_prometheus_http_server(addr=”0.0.0.0", port=9330) log.debug(“Started Prometheus server on port 9330.”) await super().start(args, *kwargs) client.run(‘WkdqnvIruKhoslqjPhRxwSZQHG’)
“Few days ago I found out a discord BOT code, can you help me out with what the bot is doing after that the flag is yours! :)”
We were also provided with the above string together with the code snippet.
The first thing that stood out to me was the client key found in the last line of the code snippet. I took a guess that it could be a result of an encryption algorithm of some sort. I fired up my goto tool, CyberChef. After trying to decrypt it with multiple algorithms, I ended up with ROT 13. However, I did not have the turn value. So I started bruteforcing and eventually found our that the value was 23.
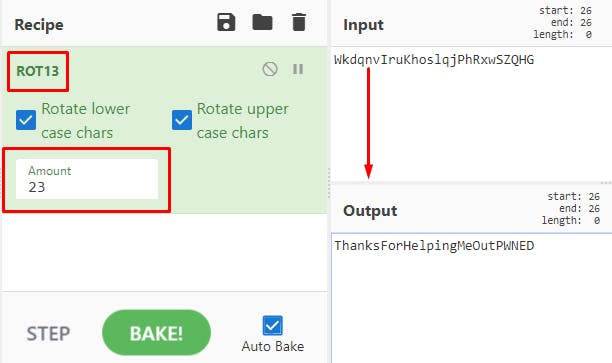
Flag — PWNDAYCTF{ThanksForHelpingMeOutPWNED}
Challenge 2— La La Land
sister was singing a song, i think she hides something! Can you find it out?
LALALLLLLLLALALLLLLLLALALLLLLLLALLLLALLLALLAAALLLAALLALLAAALALALLLAALLLLALLLLLAALLLLLALLALLLLLLALLLALALLALALALLLLLLLALALLLLLLLALALLLLLL
Erm w0t…..yea that was the same reaction I had when I first came across this challenge. After about 30 mins of researching, I discovered that this was Bacon cipher. This was the first time I was hearing about such cipher. Following the discovery, I fired up Cryptii to try and decrypt it.
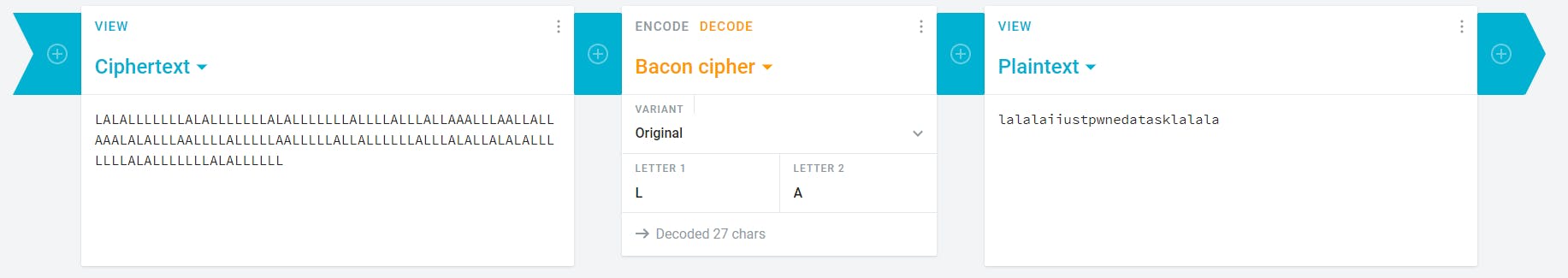
After Setting “L” as letter 1 and “A” as letter 2. That gave me the flag for this challenge
Flag — PWNDAYCTF{LaLaLaIJustPwnedATaskLaLaLa}
Challenge 3— 13th
This should be easy.. ebg13vffghcvqyby
As the text suggested, this challenge actually turned out to be pretty simple. The title “13th” got me thinking if this could be related to ROT 13….so I went right back to cyber chef to check if that was the encryption algorithm being used.
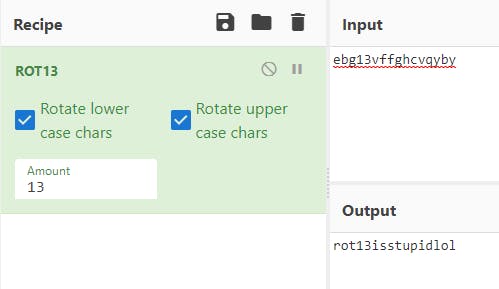
Flag — PWNDAYCTF{rot13isstupidlol}
Challenge 4–My Old Friend Jhonny
I hacked a server last night and i found out a backup of root's password! But i cant crack it...... can u help me ? After that the flag is yours.
$6$root$8u7I64NHnAq8bz/Ihl2UDGE2wKHZlHlhQesNehuq4dajROd9npVZor.NpO4YBU4sxezAKvlZQ.5ftQZIODrju0
After reading the title of the challenge, the first thing that came to my mind was the Linux based tool, JohnTheRipper. I quickly grabbed my trusty wordlist and ran john on the password hash. Surprise surprise! I got the flag.
root@kali:~/Desktop# john — wordlist=wordlist.txt passwd
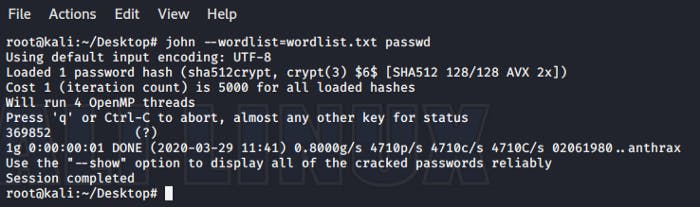
Flag — PWNDAYCTF{369852}
Challenge 5–Evil Recipe
9iOGOEMS0:,5^:;):[.9ibq)@oYBiAOpcU:KD:J<c)YQ@7<pm@rsn=]eK@;8h1;)!6>r<&%6rA6;,T:2XlmAOUES@RYT;L1fQ9mU;+=)2>J@kpMu>$#f$>!u+S9h7lW>#]08`N!S:.7cF9gqW1@;9UI@PDbC@RNgB@5CMn<CBSQ@oum:.SPf:.7cuAStOfGP3!@okNa<Cf_]=%5qY9is_s:/tg_=)E%u9iu(%:,#:09iu?mA84h9iXYQ<C]f%
32 -> 58 -> -> 62 -> 64 -> 85 ??
The title of this challenge pointed me towards my CyberChef again (geddit?? recipe, cyberchef). I was wondering what the numbers below the encrypted ciphertext mean. Then after pondering for a while, I concluded that they were related to the BASE encoding.
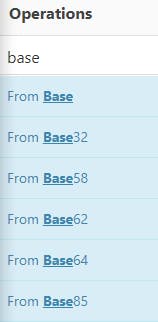
So I decided to decode the encoded text following the number and the arrow. This led me straight to the flag as seen below.
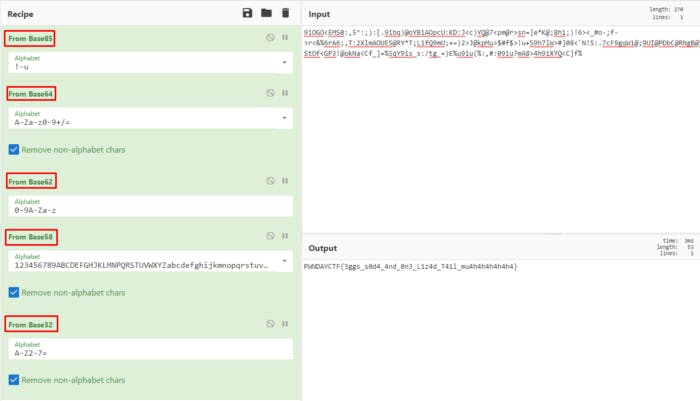
Flag — PWNDAYCTF{3ggs_s0d4_4nd_0n3_L1z4d_T41l_mu4h4h4h4h4h4}
Stego Challenges
Challenge 1 — b33r

I was only given this image by the challenge creator. I had to somehow get a flag from this image. Since this was a stego challenge, I thought of using the Strings tool to inspect the image for hidden texts. That's exactly what I did.
root@kali:~/Desktop# strings b33r.jpg > output.txt

At the end of the output, I was able to see what looked like a base 64 encoded string. I then fired up CyberChef again and tried to get the flag.
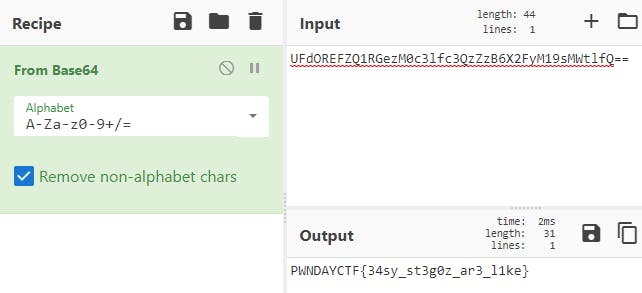
Flag — PWNDAYCTF{34sy_st3g0z_ar3_l1ke}
Challenge 2— Cookie

Give a “cookie” to the dog and you will get the flag. :)
I was only given this image and this string of text by the challenge creator. I had to somehow get a flag from this image. The phrase “give a cookie” sounded a bit off to me. I started thinking of what could that mean. I ended up with something along the lines of…….cookie is the password and I have to enter it to get the flag. So I went off to try just that.
After some research, I found a tool called Steghide. I used this to extract the data from the picture.
root@kali:~/Desktop# steghide info cookie.jpg
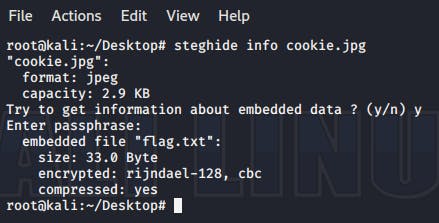
This command revealed to us that there was a file named “flag.txt” hidden inside the image but we need to enter another command in order to extract the file.
root@kali:~/Desktop# steghide extract -sf cookie.jpg Enter passphrase: wrote extracted data to "flag.txt".
root@kali:~/Desktop# cat flag.txt PWNDAYCTF{yummy_yummy_thank_you}
At the end of the output, I was able to see what looks like a base 64 encoded string. I then fired up CyberChef again and tried to get the flag.
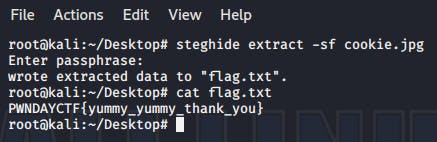
Flag — PWNDAYCTF{yummy_yummy_thank_you}
Challenge 3— Nyan cat

I was only given this image by the challenge creator. I had to somehow get a flag from this image. I did the same thing as I did for the first challenge. I fired up strings and analyzed the image again
root@kali:~/Desktop# strings Nyan\ cat.jpg > output.txt
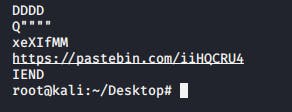
At the end of the output, I was able to see what looked like Pastebin link so I followed it.
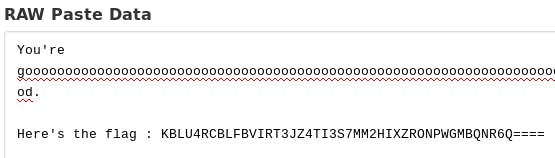
This looked like a Base encoding to me so I fired up CyberChef again. It ended up being a Base32 encoding. So I decoded it and got the flag.
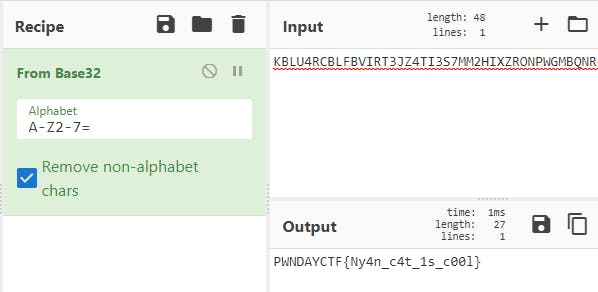
Flag — PWNDAYCTF{Ny4n_c4t_1s_c00l}
Challenge 4— Broken QR

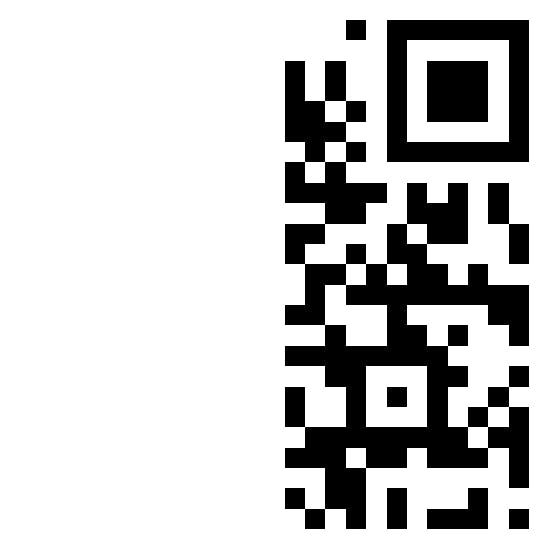
I was given a broken QR code. It was in 2 pieces. I quickly launched photoshop to try and patch it up!
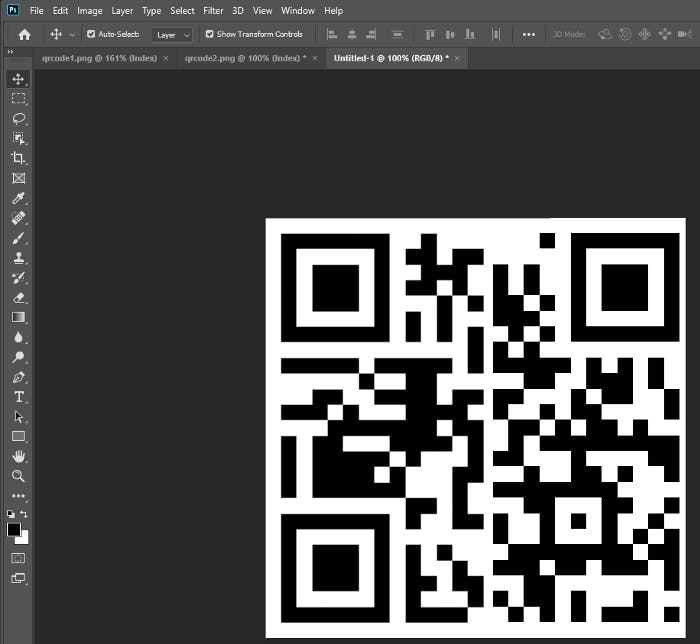
After I successfully patched it together, I used my phone to scan the code and get the flag!
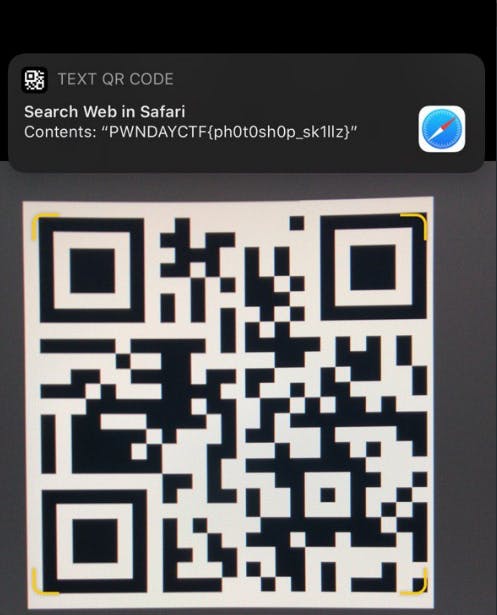
Flag — PWNDAYCTF{ph0t0sh0p_sk1llz}
Challenge 5— Flags Everywhere
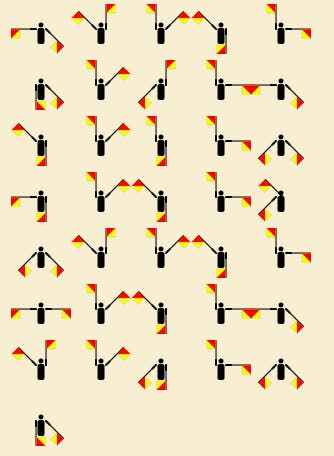
I was only given this image by the challenge creator. I had to somehow get a flag from this image. After a TON of research, I found out that this was “Flag semaphore”. I used the character set to decrypt this message and derive the flag.
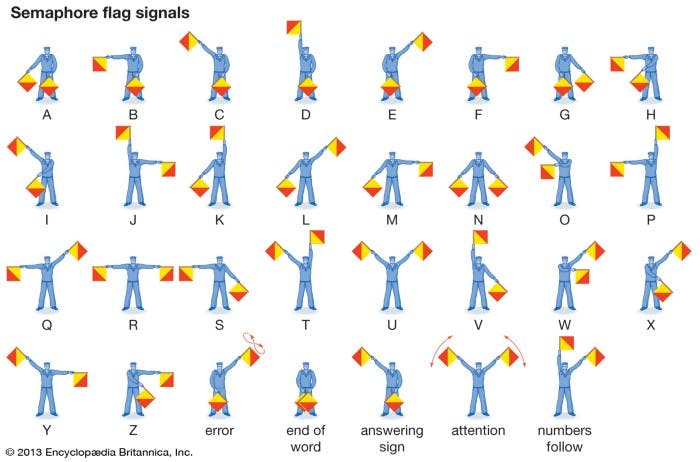
Flag — PWNDAYCTF{St3g0sC4nB3Int3r3st1ng}
Misc Challenges
Challenge 1 — Tree
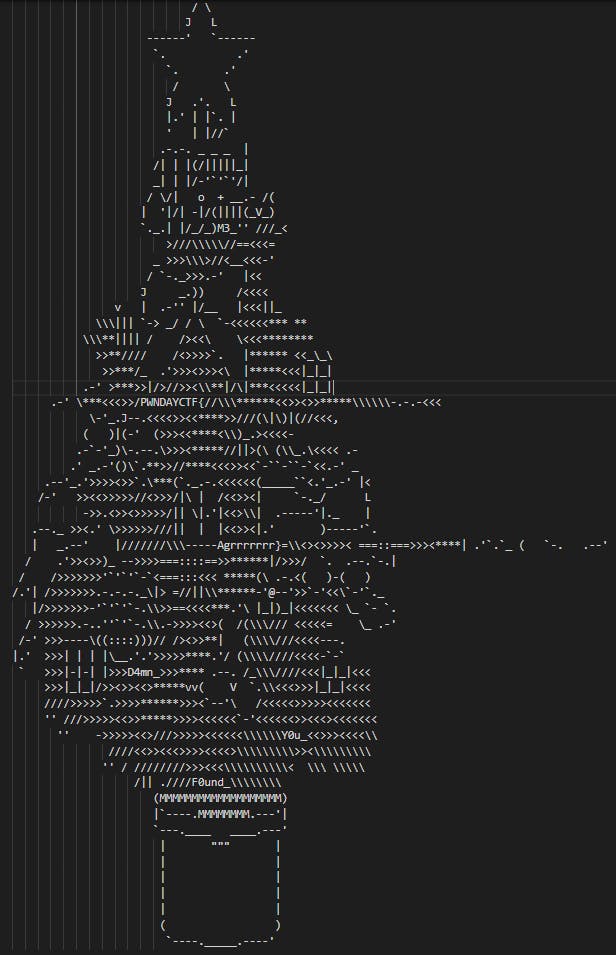
I was only given this ASCII signature/text by the author of the challenge. I went ahead and analyzed it with my naked eyes. No tools needed for this challenge. I was able to retrieve the flag.
Flag — PWNDAYCTF{D4mn_Y0u_F0und_M3_Agrrrrrrr}
Challenge 2— Xor
39–39–38–2d-32–30–21–38–23–12–5f-18–36–07–01–51–33–56–07–0a-29–58–00–07–16–33–0c-07–18–1f-1a-1a-0b-0e-09–18
Key is invisible sadly :(
The description of this challenge was oddly suspicious and reminded me of challenge 2 from Stego Challenges. However, the title of this challenge was XOR. I used Dcode instead of CyberChef this time around. I input the xor cipher into the field and entered “invisible” for the ASCII key. It worked!
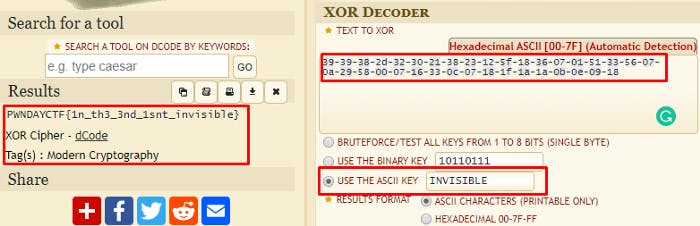
Flag — PWNDAYCTF{1n_th3_3nd_1snt_invisible}
Challenge 3— Alphanumeric
ABABAAAA ABABABBB ABAABBBA ABAAABAA ABAAAAAB ABABBAAB ABAAAABB ABABABAA ABAAABBA ABBBBABB ABBAAABA AABBAAAB ABBABBBA AABBABAA ABBBAABA ABBBBAAB ABABBBBB ABBAABBA ABBBABAB ABBABBBA ABBBBBAB
This challenge just had As and Bs. I was supposed to make a flag out of these. The first thing that came to my mind was converting it to 1s and 0s. Credits to a friend of mine [Synth#39**] who wrote a python script to do this.
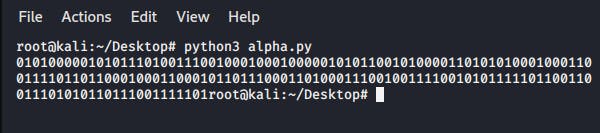
I then converted these binary numbers to text and ended up getting the flag!
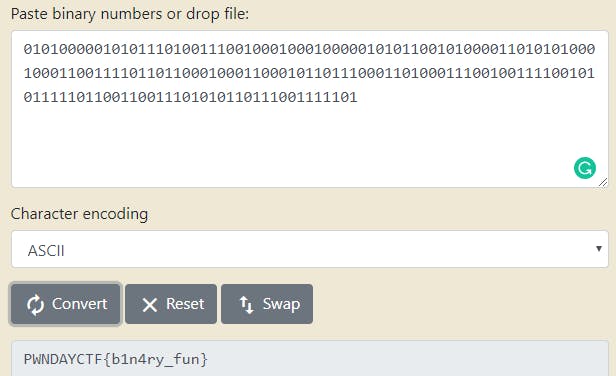
Flag — PWNDAYCTF{b1n4ry_fun}
Challenge 4— Black

This was the picture I was provided with. The flag was hidden in plain sight for this flag. I had to tweak the image settings using the windows photos app

Flag — PWNDAYCTF{BL4CK_1S_4RT}
Challenge 5— Pure ART
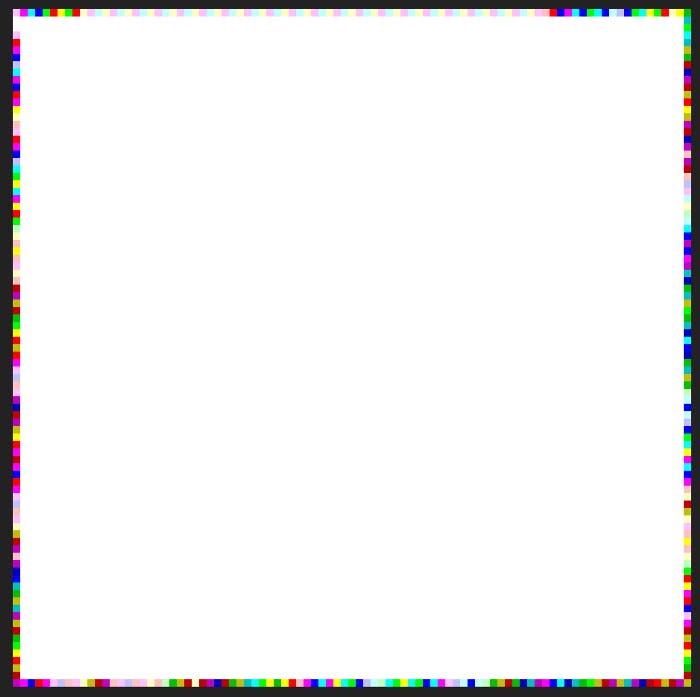
This was the picture I was provided with for this challenge. The flag was hidden inside this picture….hmmm. I went about researching online for something similar but I couldn't find much. After a couple hours of searching, I came across something called “Piet Program”. It was basically hiding strings of texts in images like this. Its like building your code into an application but in this case, the image is the code……COOL RIGHT?! Eventually, I found this site that executes piet programs like these. I successfully ended up with the flag after executing the image.
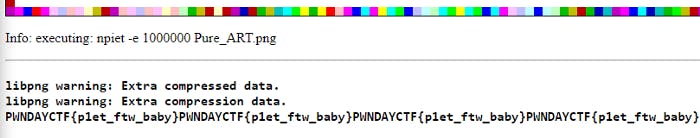
Flag — PWNDAYCTF{p1et_ftw_baby}
Web Challenges
Challenge 1 — Flag Hunting
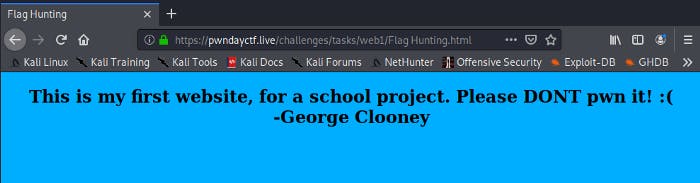
This was what I was greeted with when I accessed the URL. As always, I looked at the HTML sources at first. There was nothing interesting. Then I made my rounds around the CSS corner. There were a couple of values that looked to be Base encoded.
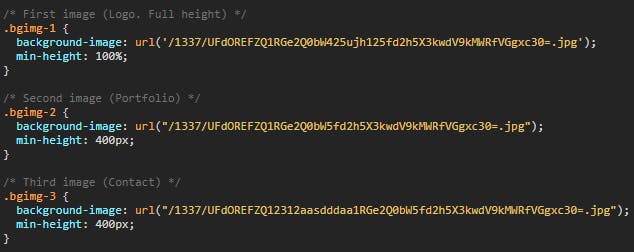
I then proceeded to decode them into bash using this command
root@kali:~# echo -n "insert_encoded_value" | base64 -d
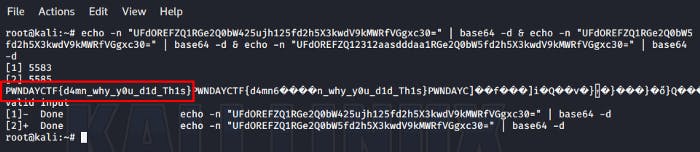
Flag — PWNDAYCTF{d4mn_why_y0u_d1d_Th1s}
Challenge 2— Ro-Ro-Ro
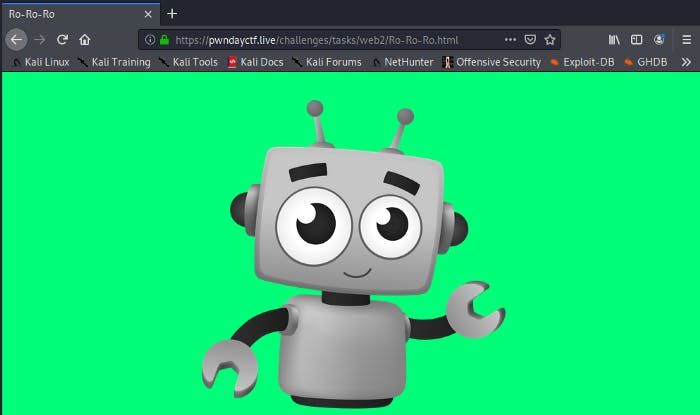
This was what I was greeted with when I accessed the URL. As always, I looked at the HTML sources at first. There was nothing interesting. Then I realized there is a picture of a robot and “robots.txt” is a file most web servers have to prevent crawlers from accessing some parts of their website. so naturally, I navigated to /robots.txt. Boom! we got the flag :)
Flag — PWNDAYCTF{1_l0v3_r0b0ts}
Challenge 3— Client Side Sucks
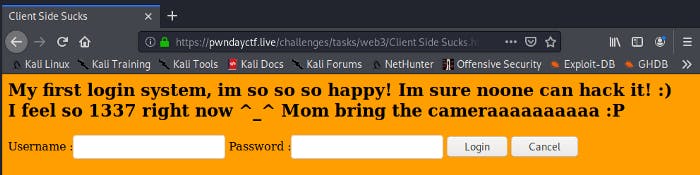
This was what I was greeted with when I accessed the URL. It was evident that I had to bypass some sort of authentication system. Thus, I looked at the source code of the website and found something very interesting. The URL which the site would direct u to after successful login was listed. Thus I headed there. And as expected, I got the flag.
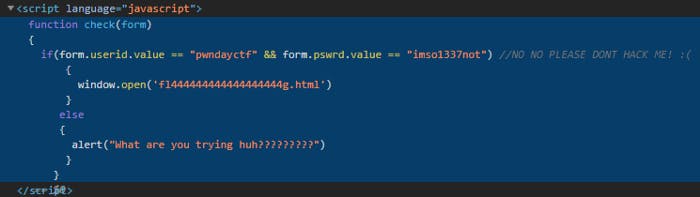
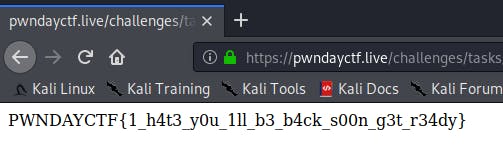
Flag — PWNDAYCTF{1_h4t3_y0u_1ll_b3_b4ck_s00n_g3t_r34dy}
Challenge 4— Client Side Sucks2
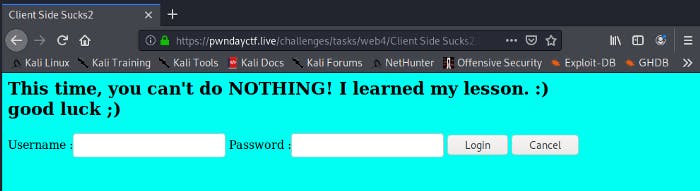
This was what I was greeted with when I accessed the URL. It was evident that I had to bypass some sort of authentication system. Thus, I looked at the source code of the website and found something very interesting. The URL which the site would direct u to after successful login was listed once again. The only difference between this challenge and the previous one was that I couldn't access the developer tab with the keyboard shortcut. The input was being blocked by the site. I just worked around that by opening it manually using the browser options.
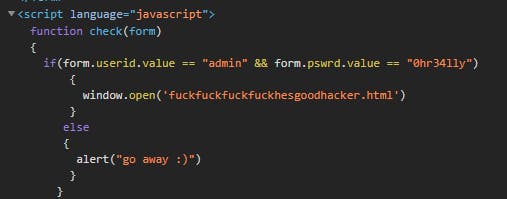

I ended up getting a Hex value. I just simply converted hexadecimal to text and got the flag.
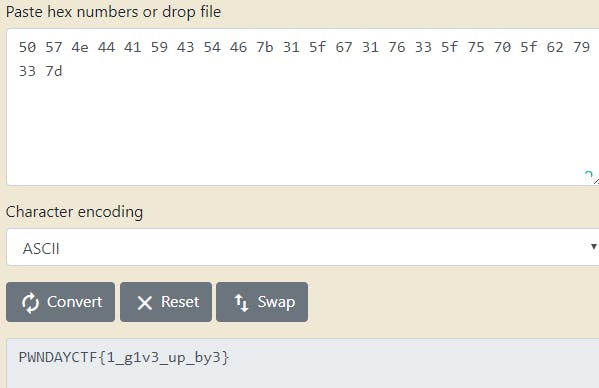
Flag — PWNDAYCTF{1_g1v3_up_by3}
Challenge 5— Elite Security
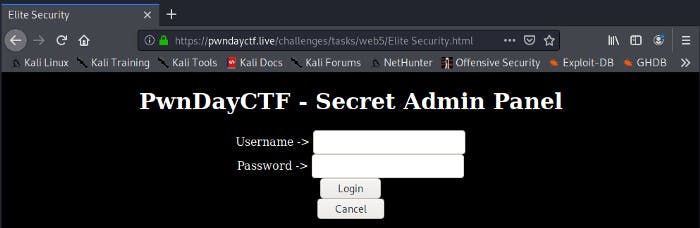
This was what I was greeted with when I accessed the URL. It was evident that I had to bypass some sort of authentication system. Thus, I looked at the source code of the website and found something very interesting. The URL which the site would direct u to after successful login was listed once again. The login code was in javascript and it was obfuscated. I spend some time beautifying the code. Here are the before and after.
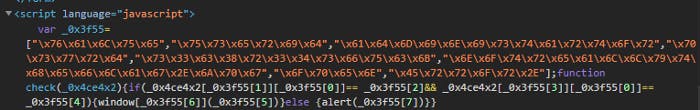
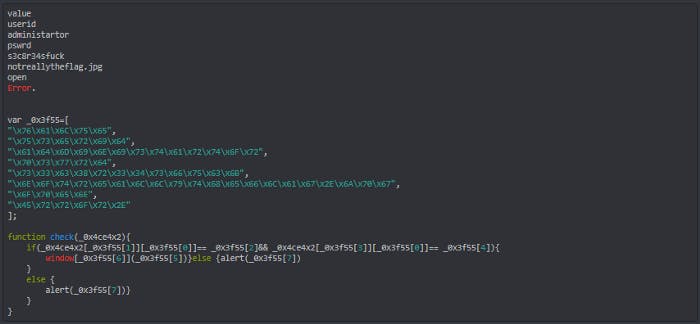
Here’s a brief explanation for this. The original code above first creates an array with the words that can be found at the top of the modified version of my code. However, these values are input as HEX values. Thus we are unable to read them. After decoding each value corresponding to the array, we figure out what the loop is trying to do. => If UserId = Administrator and Pswrd=s3c8r34sfuck, let them in. This was a good effort by the web dev but was not that hard to crack. After cracking the code, I entered the username and password to log in.
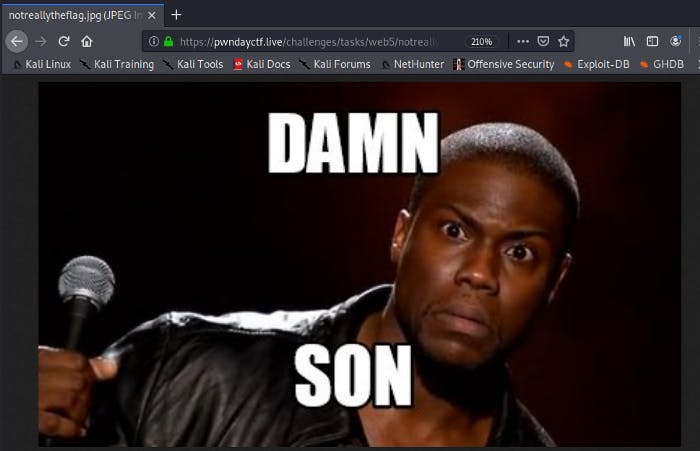
I was greeted with this image instead of the flag. After pondering for a while, I decided to download this image and run the strings tool that I used in the stego challenges.
root@kali:~/Desktop# strings notreallytheflag.jpg > output.txt
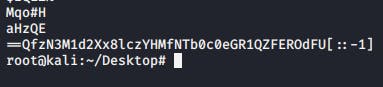
Whilst examining the output, I realized that there was a flipped string encoded with base 64. I quickly got a script to help flip the text so that I could decode it. After that, I decoded the string and successfully got the flag.
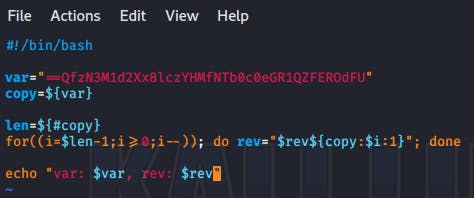
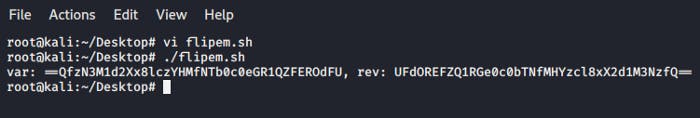
root@kali:~/Desktop# echo "UFdOREFZQ1RGe0c0bTNfMHYzcl8xX2d1M3NzfQ==" | base64 -d
PWNDAYCTF{G4m3_0v3r_1_gu3ss}
Flag — PWNDAYCTF{G4m3_0v3r_1_gu3ss}
Anddddd...that was how I successfully completed this CTF challenge!

