I recently started working at a huge company as part of my Student internship Program. Its been a 3 weeks as of writing this and I started missing the accessibility I got from using my own workstation at home. The office laptop had its own set of security policies which I totally understand. Thus, I started plotting on how I could be at home while being at the office at the same time. This is what I successfully came up with. Lets get to it 😊!
Prerequisites
- Raspberry Pi 4 – 4G Model B
- Ubuntu Server Image for pi4 – From here
- OpenVPN Connect Client – For clients
Topology
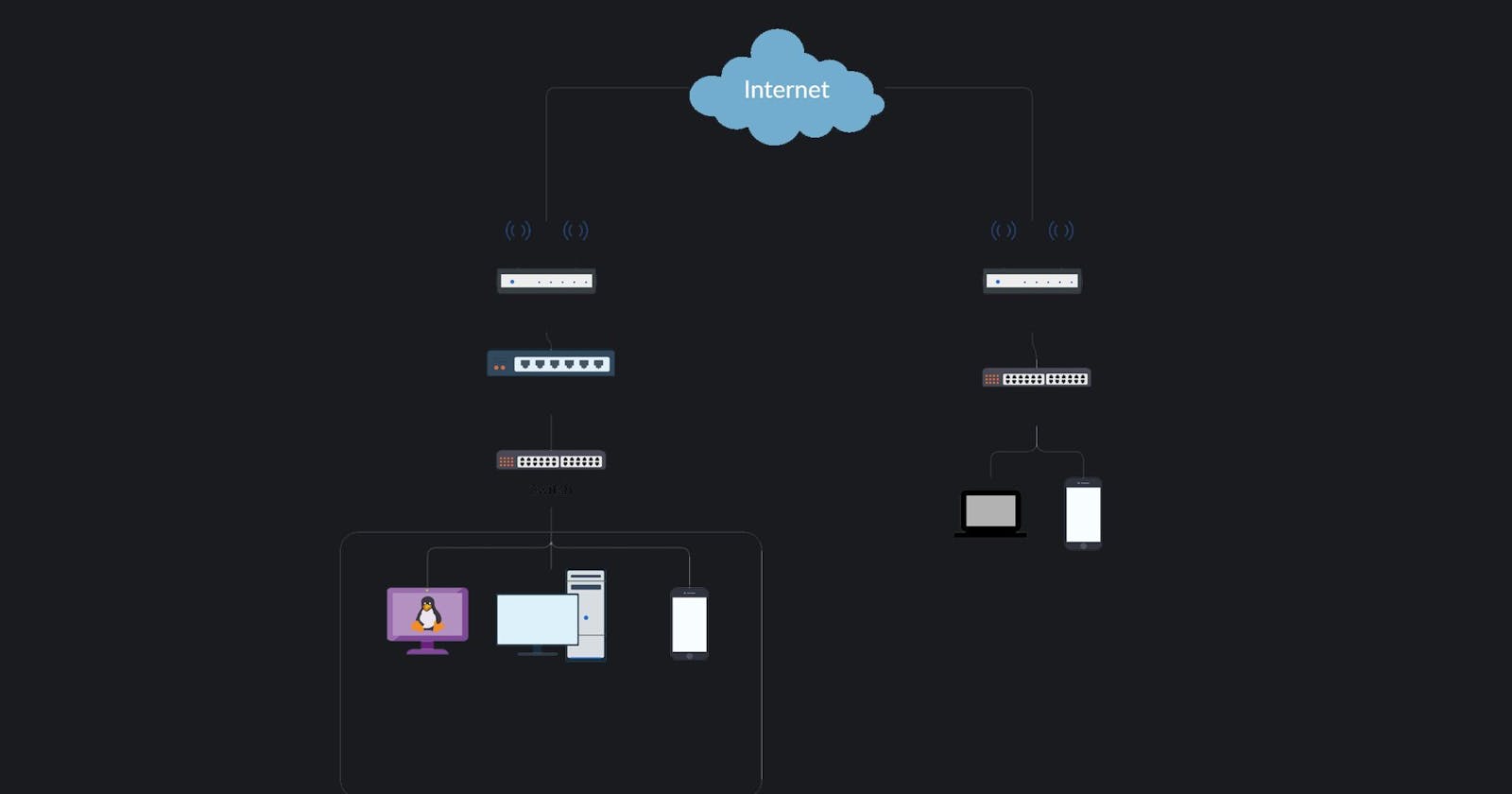
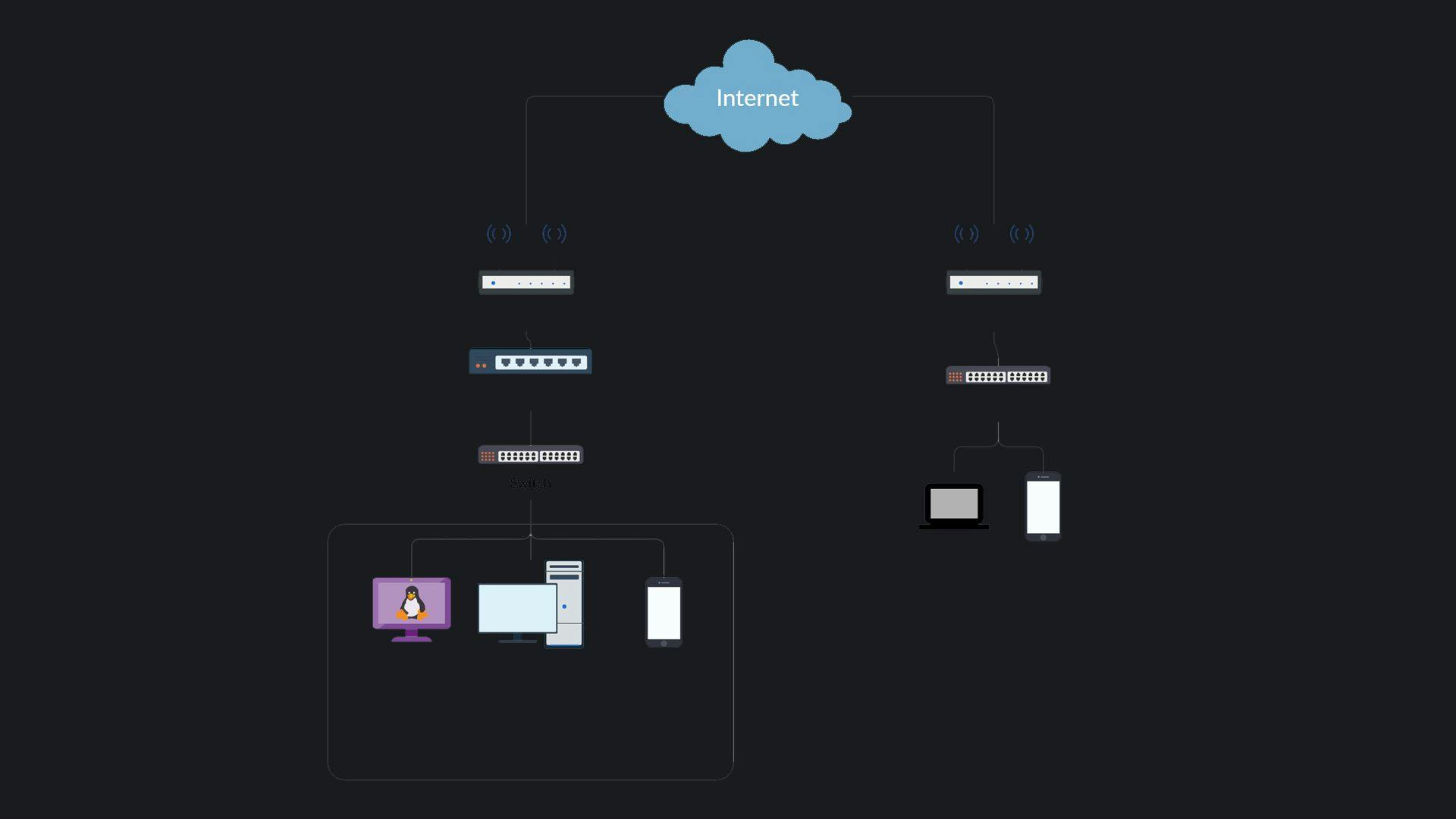
This was the topology I ended up successfully implementing. I will also reference this topology various times throughout the post.

Nee's somewhat meh topology
So, here's how everything works...
A Raspberry Pi running Ubuntu Server will be hosting an OpenVPN and SSH Server. This will act as the main point of contact for the remote client. The Ubuntu Server will then route the OpenVPN LAN [10.8.0.0/24] to the Local LAN of my home network [192.168.0.1/24]
My main workstation will be allowing any incoming RDP / SSH traffic from the internal network. My main pc will also be utilized to manage the Ubuntu Server VIA SSH. My main workstation also has Wake-On-Lan enabled. Its a technology that allows me to power on the PC by just sending a magic packet to it from anywhere in the world. You can read more about it here if you're interested! P.S. You will need a Wake-On-Lan Capable motherboard to do this.
My android 10 device will also be utilized to manage the Ubuntu Server via SSH and test if VPN is up and running. VPN should also work for any mobile device despite their location.
Overall, 4 ports are forwarded.
- Port 7 (Wake-On-Lan)
- Port 9 (Wake-On-Lan)
- Port 22 (SSH Server)
- Port 1149 (OpenVPN Server)
Ubuntu Server
I started off by installing Ubuntu Server Edition (20.04) on the Raspberry Pi. Followed by that, I setup SSH on it so that I would be able to connect to it and configure over LAN from another machine. I wouldn't need a separate monitor and peripherals for the Pi.
Next up, I setup OpenVPN on the Ubuntu Server using a guide I wrote couple months ago which can be found here! The steps are more or less about the same. Skip to the Installing /~/ Configuring OpenVPN section on the other post if you are following along.
Lastly, now that I had the tunnel up and running, I needed to route the remote clients into the local network. I had to modify the config files and add an IP tables entry. This step took me about an hour of research but I was able to get it working once this was settled.
Modifying OpenVPN Config File
root@ubuntu:~# vi /etc/openvpn/server/server.conf
local 192.168.0.131 port 1194 proto udp dev tun ca ca.crt cert server.crt key server.key dh dh.pem auth SHA512 tls-crypt tc.key topology subnet server 10.8.0.0 255.255.255.0 push "redirect-gateway def1 bypass-dhcp" ifconfig-pool-persist ipp.txt push "dhcp-option DNS 1.1.1.1" push "dhcp-option DNS 1.0.0.1" keepalive 10 120 cipher AES-256-CBC user nobody group nogroup persist-key persist-tun status openvpn-status.log verb 3 crl-verify crl.pem explicit-exit-notify push "route 192.168.0.0 255.255.255.0"
The last line is the only entry I had to enter here
Adding IP Tables rule
root@ubuntu:~# iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
I routed the traffic to my eth0 adapter as that's the adapter that's connected to my Internal LAN. If you are following along make sure to change according to your topology!
Creating Bash Script to power on pc from anywhere
root@ubuntu:~# echo "wakeonlan DE:AD:BE:EF:00:00" >> bootpc.sh chmod +x bootpc.sh

Mac address blurred for obvious reasons
Be sure to replace DE:AD:BE:EF:00:00 with your mac address if you wanna be able to wake your PC!
Main Pc Setup
There isn't much to do on this machine other than Enabling Wake on Magic Packet (Wake-On-Lan) and Remote Desktop Protocol. Keep in mind, you would need Windows 10 PRO or ENTERPRISE for the latter feature.

On windows machine

Enabling RDP
Port Forwarding
Now that all the services are running, its time to port forward all needed ports to allow incoming traffic via the public IP.

Router B

Router A
Tunneling into Internal Network from a Public Network
The first thing to do was to install the OpenVPN Connect Client from here. Followed by that, I installed the OpenVPN profile which was generated for my client after setting up OpenVPN and successfully connected!


I was able to successfully communicate with my personal workstation at home VIA the tunnel. Next thing was to test If I was able to RDP into it.

RDP connection to personal workstation at home
Lastly I tested if I was able to wake my personal workstation VIA an SSH connection to the ubuntu server using the bash script I had created before. As expected It worked too!
And that's the end! I was able to successfully setup a tunnel back to my home from anywhere and connect to my personal workstation VIA rdp and so on 😊 Hope this was some kind of help to you!
~Nee